
SonicWall®SecureMobileAccess
8.6WebApplicationFirewall
FeatureGuide

SonicWallSMA8.6WebApplicationFirewallFeatureGuide
Contents
1
2
DocumentScope ................................ . . ..................................4
LicensingWebApplicationFirewall ............................
.............. . ..........5
Overview.........................
.............. . ..................................8
Whatis
WebApplicationFirewall?............... ..................... ................... 8
BenefitsofWebApplicationFirewall.....................................
................ 11
HowDoesWebApplicationFirewallWork?............... .............
............... ....11
HowareSignaturesUsedtoPreventAttacks? ........................
..................12
HowisCross‐SiteRequestForgeryPrevented? ............... ..........
................ 14
HowisInformationDisclosurePrevented?.. ..................... ......
............... 14
HowareBrokenAuthenticationAttacksPrevented?.............................
....... 15
HowareInsecureStorageandCommunicationsPrevented?.............................15
HowisAccesstoRestrictedURLsPrevented?
... ..................... .................. 15
HowareSlowlorisAttacksPrevented? ...
................................... ..........15
WhatTypeofPCICompliance
ReportsAreAvailable?................................. ..16
HowDoesCookieTamperingProtectionWork?......
.................................. 16
HowDoesApplicationProfilingWork?...........
.................................... 18
HowDoesRateLimitingforCustomRulesWork?......
................................. 19
SupportedPlatforms ...............
................................... ................ 20
ConfiguringWebApplicationFirewall ....................................... . . ....
.....21
ViewingandUpdatingWebApplicationFirewallStatus..................................... 21
ViewingStatus
andSynchronizingSignatures ................................... .. .....22
DownloadingaPCIComplianceReport
................... ..................... .. .....22
ConfiguringWebApplication
FirewallSettings ............................................. 23
EnablingWebApplication
FirewallandConfiguringGeneralSettings...................... 24
ConfiguringGlobal Exclusions ....................
................................... 25
ConfiguringIntrusionPreventionErrorPageSettings.........
........................... 26
ConfiguringCross‐SiteRequestForgeryProtectionSettings............ ....
.............. 27
ConfiguringCookieTampering P rotectionSettings.............. .................
....... 28
ConfiguringWebSiteCloaking.......................................
............... 29
ConfiguringInformationDisclosureProtection ...............................
.......... 30
ConfiguringSessionManagementSettings............... .....................
........ 31
ConfiguringWebApplicationFirewallSignatureActions . ..................... ..............
.32
EnablingPerformanceOptimization............................. .................
....33
ConfiguringSignatureBasedCustomHandlingand Exclusions........ .. .................. 33
RevertingaSignaturetoGlobalSettings....
..........................................35
RemovingaHostfromaPer‐SignatureExclusion
............... ........................35
DeterminingtheHostEntryforExclusions.....
............... ..................... .......35
ViewingtheHostEntryinaBookmark
................................................ 36
Viewingthe
HostEntryinanOffloadedApplication..................................... 37
ConfiguringCustomRulesandApplicationProfiling.
............... ........................38
ConfiguringApplicationProfiling........
............... ..................... ........40
Contents

SonicWallSMA8.6WebApplicationFirewallFeatureGuide
Contents
3
ConfiguringRuleChains....... ..................... ................................43
ConfiguringRulesinaRuleChain ................................
....................45
UsingWebApplicationFirewallMonitoring................ .........
......................55
MonitoringontheLocalScreen...................... .
.............................. 55
MonitoringontheGlobalScreen ...............
................................... ..60
UsingWebApplicationFirewallLogs ........
................................... .......... 62
SearchingtheLog..
................................... ............................63
ControllingtheLogPagination.. ..................... ..........
.....................63
ViewingLogEntryDetails.........................
............... .................. 64
ExportingandEmailingLogFiles............
........................................64
ClearingtheLog.......
............... ..................... .......................65
ConfiguringanApplicationOffloadingPortal.. .. ..................... ............
......... 65
VerifyingandTroubleshootingWebApplicationFirewall..................................70
SonicWall
Support ......................................................... .........72
AboutThisDocument................................
................................. 73

SonicWallSMA8.6WebApplicationFirewallFeatureGuide
DocumentScope
1
4
DocumentScope
ThisdocumentdescribeshowtoconfigureandusetheWebApplicationFirewallfeatureinSonicWall®Secure
MobileAccess(SMA)8.6.
Thisdocumentcontainsthefollowingsections:
• Overviewonpage8
• LicensingWebApplicationFirewallonpage5
• ConfiguringWebApplicationFirewallonpage21
• VerifyingandTroubleshootingWebApplicationFirewallon
page70

SonicWallSecureMobileAccess8.6FeatureGuide
LicensingWebApplicationFirewall
2
5
LicensingWebApplicationFirewall
SonicWallSMA/SRAWebApplicationFirewallmustbelicensedbeforeyoucanbeginusingit.Youcanaccessthe
MySonicWallwebsitedirectlyfromtheSonicWallSMA/SRAmanagementinterfacetoobtainalicense.
TheWebApplicationFirewall>LicensingpageintheSonicWallSMAmanagementinterfaceprovidesalinkto
theSystem
>Licensespage,whereyoucanconnecttoMySonicWallandpurchasethelicense orstartafree
trial.YoucanviewallsystemlicensesontheSystem>Licensespageofthemanagementinterface.
ToviewlicensedetailsandobtainalicenseonMySonicWallforWebApplicationFirewall:
1LogintoyourSonicWallSMA/SRAapplianceandnavigatetoWebApplicationFirewall>Licensing.
2IfWebApplicationFirewallisnotlicensed,clicktheSystem>Licenseslink.TheSystem>Licensespageis
displayed.

SonicWallSecureMobileAccess8.6FeatureGuide
LicensingWebApplicationFirewall
6
3UnderManageSecurityServicesOnline,clicktheActivate,Upgrade,orRenewserviceslink.The
MySonicWallLoginpageisdisplayed.
4TypeyourMySonicWallcredentialsintothefields,andthenclickSubmit.TheManageServicesOnline
tableisdisplayed.
5 ClickTrytostarta180dayfreetrial,orclickActivatetosubscri be
totheservicefor1year.Thescreen
belowisdisplayedafterselectingthefreetrial.

SonicWallSecureMobileAccess8.6FeatureGuide
LicensingWebApplicationFirewall
7
6 ClickSynchronizetoviewthelicenseontheSystem>Licensespage.
WebApplicationFirewallisnowlicensedonyourSonicWallSMA/SRAappliance.NavigatetoWebApplication
Firewall>Settingstoenableit,andthenrestartyourappliancetocompletelyactivateWebApplicationFirewall.

SonicWallSecureMobileAccess8.6FeatureGuide
Overview
3
8
Overview
ThissectionprovidesanintroductiontotheWebApplicationFirewallfeature.Thissectioncontainsthe
followingsubsections:
• WhatisWebAppli cationFirewall?onpage8
• BenefitsofWebApplicationFirewallonpage11
• HowDoesWebApplicationFirewallWork?onpage11
• SupportedPlatformsonpage20
WhatisWebApplicationFirewall?
WebApplicationFirewallissubscription‐basedsoftwarethatrunsontheSonicWallSMAapplianceandprotects
webapplicationsrunningonserversbehindtheappliance.WebApplicationFirewallalsoprovidesreal‐time
protectionforresourcessuchasHTTP(S)bookmarks,Citrixbookmarks,webapplicationsrunningonApplication
Offloadingportals,andtheSMAmanagement
interfaceanduserportalthatrunontheSonicWallSMA
appliance.
TheDefinitionsofTermstableprovidesdefinitionsofterminologyrelatedtoSonicWallSMAWebAppli cation
Firewall.
WebApplicationFirewallprovidesreal‐timeprotectionagainstawholesuiteofwebattackssuchasCross‐site
scripting,SQLInjection,OSCommandInjection,
andmanymore.Thetoptenvulnerabilitiesforwebapplications
aretrackedbyOWASP,anopensourcecommunitythatfocusesitseffortsonimprovingthesecurityofweb
DefinitionsofTerms
Term Definition
WebApplicationFirewall Securitytechnologythatisplacedbetweenawebserverandtheinternetthat
analyzeslayer7traffic
sessionstoprotectapplicationsfrominboundattacks.A
WebApplicationFirewalldeterminesaccesspermissionsbasedonapre‐defined
setofstandardandcustomrules.
ApplicationOffloading ApplicationOffloadingisthetechniqueofportingpartofanapplicationtoa
nearbyserverorworkstationwithmorecapabilitiesthanthedevicethatwill
run
theapplication,suchasaPDAormobilephone.Suchaserverisoften
public‐facing,andmayneedprotectionfromattacks.Offloadedapplications
operateinseamlessmodeinwhichtheURLsintheproxiedpagearenot
rewrittenbytheproxyserver.
ReverseProxy Aproxyserverthatisdeployed
betweenoneormoreservers(oftenwebservers)
andtheinternet.Allconnectionscomingfromtheinternetinboundtooneofthe
webserversareroutedthroughtheproxyserver,presentingasingleinterfaceto
externalusers.Thereverseproxyservercanfulfillarequestitselforpassthe
requestto
themainservers.
HTTP(S)ReverseProxy ThisreverseproxyinterceptsHTTP(S)requestsandresponses.

SonicWallSecureMobileAccess8.6FeatureGuide
Overview
9
applications.SonicWallSMAWebApplicationFirewallprotectsagainstthesetoptenvulnerabilities,definedin
2007asfollows:
SlowlorisProtection
Inadditiontothetoptenthreatslistedabove,WebApplicationFirewallprotectsagainstSlowlorisHTTPDenial
ofServiceattacks.ThismeansthatWebApplicationFirewallalsoprotectsallthebackendwebserversagainst
thisattack.Manywebser vers,includingApache,arevulnerabletoSlowloris.Slowlorisisespeciallyeffective
againstweb
serversthatusethreadedprocessesandlimittheamountofthreadingallowed.
OW ASPTopTenVulnerabilities
Name Description
A1‐CrossSiteScripting(XSS) XSSflawsoccurwheneveranapplicationtakesusersupplieddataand
sendsittoawebbrowserwithoutfirstvalidatingorencodingthat
content.XSSallowsattackerstoexecutescripts
inthevictim'sbrowser
whichcanhijackusersessions,defacewebsites,andpossibly
introduceworms.
A2‐InjectionFlaws Injectionflaws,particularlySQLinjection,arecommoninweb
applications.Injectionoccurswhenuser‐supplieddataissenttoan
interpreteraspartofacommandorquery.Theattacker'shostiledata
tricks
theinterpreterintoexecutingunintendedcommandsor
changingdata.
A3‐MaliciousFileExecution Codevulnerabletoremotefileinclusion(RFI)allowsattackersto
includehostilecodeanddata,resultingindevastatingattacks,suchas
totalservercompromise.MaliciousfileexecutionattacksaffectPHP,
XMLandanyframeworkwhichacceptsfilenames
orfilesfromusers.
A4‐InsecureDirectObjectReference Adirectobjectreferenceoccurswhenadeveloperexposesa
referencetoaninternalimplementationobject,suchasafile,
directory,databaserecord,orkey ,asaURLorformparameter.
Attackerscanmanipulatethosereferencestoaccessotherobjects
withoutauthorization.
A5‐CrossSiteRequestForgery(CSRF) ACSRFattackforcesalogged‐onvictim'sbrowsertosenda
pre‐authenticatedrequesttoavulnerablewebapplication,which
thenforcesthevictim'sbrowsertoperformahostileactiontothe
benefitofthea ttacker.CSRFcanbeaspowerfulasthe
webapplication
thatitattacks.
A6‐InformationLeakageand
ImproperErrorHandling
Applicationscanunintentionallyleakinformationabouttheir
configuration,internalworkings,orviolateprivacythroughavarietyof
applicationproblems.Attackersusethisweaknesstostealsensitive
data,orconductmoreseriousattacks.
A7‐BrokenAuthenticationand
SessionManagement
Account
credentialsandsessiontokensareoftennotproperly
protected.Attackerscompromisepasswords,keys,orauthentication
tokenstoassumeotherusers'identities.
A8‐InsecureCryptographicStorage Webapplicationsrarelyusecryptographicfunctionsproperlyto
protectdataandcredentials.Attackersuseweaklyprotecteddatato
conductidentitytheftandothercrimes,such
ascreditcardfraud.
A9‐InsecureCommunications Applicationsfrequentlyfailtoencryptnetworktrafficwhenitis
necessarytoprotectsensitivecommunications.
A10‐FailuretoRestrictURLAccess Frequently,anapplicationonlyprotectssensitivefunctionalityby
preventingthedisplayoflinksorURLstounauthorizedusers.
Attackerscanusethisweakness
toaccessand performunauthorized
operationsbyaccessingthoseURLsdirectly.

SonicWallSecureMobileAccess8.6FeatureGuide
Overview
10
Slowlorisisastealthy,slow‐actingattackthatsendspartialHTTPrequestsatregularintervalstohold
connectionsopentothewebserver.Itgraduallytiesupallthesockets,consumingsocketsastheyarefreedup
whenotherconnectionsareclosed.Slowloriscansenddifferenthostheaders,andcansend
GET,HEAD,and
POSTrequests.ThestringofpartialrequestsmakesSlowloriscomparabletoaSYNflood,exceptthatituses
HTTPratherthanTCP.Onlythetargetedwebserverisaffected,whileotherservicesandportsonthesame
serverarestillavailable.Whentheattackisterminated,the
webservercanreturntonormalwithinaslittleas5
seconds,makingSlowlorisusefulforcausingabriefdowntimeordistractionwhileotherattacksareinitiated.
Oncetheattackstopsorthesessionisclosed,thewebserverlogsmayshowseveralhundred400errors.
Formoreinformationabouthow
WebApplicationFirewallprotectsagainsttheOWASPtoptenandSlowloris
typesofattacks,seetheHowDoesWebApplicationFirewallWork?onpage11.
OffloadedWebApplicationProtection
WebApplicationFirewallcanalsoprotectanoffloadedwebapplication,whichisaspecialpurposeportal
createdtoprovideseamlessaccesstoawebapplicationrunningonaserverbehindtheSMA/SRAappliance.
Theportalmustbeconfiguredasavirtualhost.Itispossibletodisableauthenticationandaccesspolicy
enforcementforsuchanoffloadedhost.Ifauthenticationisenabled,asuitabledomain needstobeassociated
withthisportalandallSonicWalladvancedauthenticationfeaturessuchasOneTimePassword,Two‐factor
Authentication,andSingleSign‐Onapplytotheoffloadedhost.
ApplicationProfiling
ApplicationProfiling(Phase1)allowstheadministratortogeneratecustomrulesinanautomatedmannerbased
onatrustedsetofinputs.Thisisahighlyeffectivemethodofprovidingsecuritytowebapplicationsbecauseit
developsaprofileofwhatinputsareacceptablebytheapplication.Everythingelseisdenied,
providingpositive
securityenforcement.Thisresultsinfewerfalsepositivesthangenericsignatures,whichadoptanegative
securitymodel.Whentheadministratorplacesthedeviceinlearningmodeinastagingenvironment,the
SMA/SRAappliancelearnsvalidinputsforeachURLaccessedbythetrustedusers.Atanypointduring
orafter
thelearningprocess,thecustomrulescanbegeneratedbasedonthe“learned”profiles.Multipleapplications
canbeprofiledsimultaneously.
RateLimitingforCustomRules
Itispossibletotracktherateatwhichacustomrule,orrulechain,isbeingmatched.Thisisextremelyusefulto
blockdictionaryattacksorbruteforceattacks.Theactionfortherulechainistriggeredonlyiftherulechainis
matchedasmanytimesasconfigured.
CookieTamperingProtection
CookieTamperingProtectionisanimportantiteminthePaymentCardIndustryDataSecurityStandard(PCI
DSS)section6.6requirementsandpartoftheWebApplicationFirewallevaluationcriteriathatoffersstrict
securityforcookiessetbythebackendwebservers.Varioustechniquessuchasencryptionandmessagedigest
areused
topreventcookietampering.
CreditCardandSocialSecurityNumberProtection
CreditCard/SSNprotectionisaDataLossPreventiontechniquethatensuresthatsensitiveinformation,suchas
creditcardnumbersandSocialSecuritynumbersarenotleakedwithinwebpages.Oncesuchleakageis
detected,theadministratorcanchoosetomaskthesenumberspartiallyorwholly,presentaconfigurableerror
page,or
simplylogtheevent.

SonicWallSecureMobileAccess8.6FeatureGuide
Overview
11
PDFReportingforWAFMonitoringandPCIDSS6.5and6.6Compliance
SPDFreportingisintroducedforWebApplicationFirewallMonitoringandPCIDSS6.5and6.6Compliance.You
cangeneratethereportsontheWebApplicationFirewall>Statuspage.Thetimelineforgeneratingthedata
publishedinthereportsisconfigurableontheWebApplicationFirewall>Monitoringpage.
BenefitsofWebApplicationFirewall
WebApplicationFirewallissecureandcanbeusedinvariousareas,includingfinancialservices,healthcare,
applicationserviceproviders,ande‐commerce.TheSonicWallSMAapplianceusesSSLencryptiontoencrypt
databetweentheWebApplicationFirewallandtheclient.SMAalsosatisfiesOWASPcryptographicstorage
requirementsbyencryptingkeysand
passwordswherevernecessary.
CompaniesusingWebApplicationFirewallcanreducethedevelopmentcostrequiredtocreatesecure
applicationsandalsocutoutthehugeturnaroundtimeinvolvedindeployinganewlyfoundvulnerabilityfixin
everywebapplicationbysigningupforWebApplicationFirewallsignatureupdates.
ResourcesaccessedoverApplication
OffloadedportalsandHTTP(S)bookmarkscanbevulnerableduetoa
varietyofreasonsrangingfrombadlydesignedarchitecturetoprogrammingerrors.WebApplicationFirewall
providesaneffectivewaytopreventahackerfromexploitingthesevulnerabilitiesbyprovidingreal‐time
protectiontowebapplicationsdeployedbehindtheSonicWallSecureMobile
Access/SRAappliance.
DeployingWebApplicationFirewallattheSMA/SRAapplianceletsnetworkadministratorsuseapplication
offloadingevenwhenitexposeswebapplicationsneedingsecuritytointernalandremoteusers.Application
offloadingavoidsURLrewriting,whichimprovestheproxyperformanceandfunctionality.
ThereareseveralbenefitsofintegratingWebApplicationFirewallwith
SonicWallSMAappliances.Firstly,
identity‐basedpolicycontrolsarecoretoWebAppl icationFirewallandthisiseasilyachievableusingthe
SonicWallSecureMobileAccesstechnology .Secondly,therearelowerlatenciesduetotheexisting
hardware‐basedSSLoffloading.Mostimportantly,SMA/SRAappliancesrunwebapplicationsandmustbe
protectedfrom
suchattacks.
Assmallbusinessesadopthostedservicestofacilitatesuppliercollaboration,inventorymanagement,online
sales,andcustomeraccountmanagement,theyfacethesamestrictcompliancerequirementsaslarge
enterprises.WebApplicationFirewallonaSonicWallSecureMobileAccess/SRAapplianceprovidesa
convenient,cost‐effectivesolution.
WebApplicationFirewalliseasy
toconfigureintheSonicWallSMAmanagementinterface.Theadministrator
canconfigureWebApplicationFirewallsettingsglobally,byattackpriority,and onaper‐signaturebasis.Once
customconfigurationsettingsorexclusionsareinplace,youcandisableWebApplicationFirewallwithoutlosing
theconfiguration,allowingyoutoperformmaintenanceor
testingandtheneasilyre‐enableit.
HowDoesWebApplicationFirewallWork?
TousetheWebApplicationFirewallfeature,theadministratormustfirstlicensethesoftwareorstartafreetrial.
WebApplicationFirewallmustthenbeenabledontheWebApplicationFirewall>Settingspageofthe
SonicWallSMAmanagementinterface.WebApplicationFirewallcanbeconfiguredtologorblockdetected
attacksarrivingfromtheinternet.
ThefollowingsectionsdescribehowWebApplicationFirewallandSonicWallSMApreventattackssuchas
SlowlorisorthoselistedintheOWASPtopten,andhowWebApplicationFirewallprotectsagainstinformation
disclosure,andothercapabilities:
• HowareSignaturesUsedtoPreventAttacks?onpage12
• HowisCross‐SiteRequestForgeryPrevented?onpage14

SonicWallSecureMobileAccess8.6FeatureGuide
Overview
12
• HowisInformationDisclosurePrevented?onpage14
• HowareBrokenAuthenticationAttacksPrevented?onpage15
• HowareInsecureStorageandCommunicationsPrevented?onpage15
• HowisAccesstoRestrictedURLsPrevented?onpage15
• HowareSlowlorisAttacksPrevented?onpage15
• WhatTypeofPCICompliance
ReportsAreAvailable?onpage16
• HowDoesCookieTa mperingProtectionWork?onpage16
• HowDoesApplicationProfilingWork?onpage18
• HowDoesRateLimitingforCustomRulesWork?onpage19
HowareSignaturesUsedtoPreventA ttacks?
ForCrossSiteScripting,InjectionFlaws,MaliciousFileExecution,andInsecureDirectObjectRef erence
vulnerabilities,theWebApplicationFirewallfeatureusesablacklistofsignaturesthatareknowntomakeweb
applicationsvulnerable.NewupdatestothesesignaturesareperiodicallydownloadedfromaSonicWall
signaturedatabaseserver,providingprotectionfrom
recentlyintroducedattacks.
Howsignaturespreventattacks
Wheninputarrivesfromtheinternet,WebApplicationFirewallinspectsHTTP/HTTPSrequestheaders,cookies,
POSTdata,querystrings,responseheaders,andcontent.Itcomparestheinputtobothablacklistandawhite
listofsignatures.Ifpatternmatchingsucceedsforanysignature,
theeventisloggedand/ortheinputisblocked
ifsoconfigured.Ifblocked,anerrorpageisreturnedtotheclientandaccesstotheresourceisprevented.The
threatdetailsarenotexposedintheURLoftheerrorpage.Ifconfiguredfordetectiononly,theattackis logged
buttheclientcanstillaccesstheresource.Ifnosignatureismatched,therequestisforwardedtotheweb
serverforhandling.

SonicWallSecureMobileAccess8.6FeatureGuide
Overview
13
Whathappenswhennosignatureismatched
TheWebApplicationFirewallprocessisoutlinedinthefollowingflowchart.
WebApplicationFirewallprocess
Inthecaseofablockedrequest,thefollowingerrorpageisreturnedtotheclient:
ThispageiscustomizableunderWebApplicationFirewall>SettingsintheSMAmanagementinterface.
Some
administratorsmightwanttocustomizetheHTMLcontentsofthispage.Othersmightnotwanttopresenta
userfriendlypageforsecurityreasons.Instead,theymightprefertheoptiontopresentanHTTPerrorcodesuch
as404(N ot found)or403(AccessDenied).

SonicWallSecureMobileAccess8.6FeatureGuide
Overview
14
HowisCross‐SiteRequestForgeryPrevented?
CSRFattacksarenotdetectedwithsignaturematching.Usingthisvulnerability,ahackerdisguisedasthevictim
cangainunauthorizedaccesstoapplicationevenwithoutstealingthesessioncookieofauser.Whi leavictim
userisauthenticatedtoawebsiteunderattack,theusermayunwittinglyloadamalicious
webpagefroma
differentsitewithinthesamebrowserprocesscontext,forinstance,bylaunchingitinanewtabpartofthe
samebrowserwindow.Ifthismaliciouspagemakesahiddenrequesttothevictimwebserver,thesession
cookiesinthebrowsermemoryaremadepart
ofthisrequestmakingthisanauthenticatedrequest.Theweb
serverservestherequestedwebpageasitassumesthattherequestwasaresultofauseractiononitssite.To
maximizethebenefits,hackerstypicallytargetactionablerequestssuchasdataupdatestocarryoutthisattack.
To
preventCSRFattacks,everyHT TPrequestwithinabrowsersessionneedstocarryatokenbasedontheuser
session.Toensurethateveryrequestcarriesthistok en,WebApplicationFirewallrewritesallURLscontainedin
awebpagesimilarlytohowtheyarerewrittenbytheReverseProxyforHTTP(S)
Bookmarksfeature.IfCSRF
protectionisenabled,thisisalsoperformedforApplicationOffloading.
CSRFprotectionisprovidedforanonymousmodeaswell.IfCSRFprotectionisenabled,thenanidletimeoutset
totheglobalidletimeoutisenforcedforanonymousaccess.Ifthesessiontimesout,anerrormessage
is
displayed,forcingtheusertorevisitthesiteinanewwindow.Ifauthenticationisenforcedfortheportal,then
theuserisredirectedtotheloginpagefortheportal.
HowisInformationDisclosurePrevented?
WebApplicationFirewallpreventsInformationDisclosureandImproperErrorHandlingbyprovidingawayfor
theadministratortoconfiguretextcontainingconfidentialandsensitiveinformationsothatnowebsite
accessedthroughtheWebApplicationFirewallrevealsthistext.ThesetextstringsareenteredontheWeb
ApplicationFirewall>Settings
page.
Besidetheabilitytopatternmatchcustomtext,signaturespertainingtoinformationdisclosurearealsousedto
preventthesetypesofattacks.

SonicWallSecureMobileAccess8.6FeatureGuide
Overview
15
WebApplicationFirewallprotectsagainstinadvertentdisclosureofcreditcardandSocialSecuritynumbers
(SSN)inHTMLwebpages.
WebApplicationFirewallcanidentifycreditcardandSSNnumbersinvariousformats.Forexample,aSSNcan
bespecifiedasXXXXXXXXXorXXX‐XX‐XXXX.WebApplicationFirewallattempts
toeliminatefalse‐positivesby
filteringoutformatsthatdonotconformtothecreditcardorSSNspecification.Forexample,creditcardsfollow
theLuhn’salgorithmtodetermineifann‐digitnumbercouldbeacreditcardnumberornot.
Theadministratorcansetanappropriateaction,suchas
detect(log),prevent,orjustmaskthedigitsthatcan
revealtheuseridentity.Maskingcanbedonefullyorpartially,andyoucanselectanyofthefollowing
charactersformasking:#,*,‐,x,X,.,!,$,and?.Theresultingmaskednumberissimilartothe
appearanceof
creditcardnumbersprintedonaninvoice.
HowareBrokenAuthenticationA ttacksPrevented?
TherequirementforBrokenAuthenticationandSessionManagementrequiresWebApplicationFirewallto
supportstrongsessionmanagementtoenhancetheauthorizationrequirementsforwebsites.SonicWallSMA
alreadyhasstrongauthenticationcapabilitieswiththeabilitytosupport OneTimePassword,Two‐factor
Authentication,SingleSign‐On,andclientcertificateauthentication.
For
SessionManagement,WebApplicationFirewallpopsupasessionlogoutdialogboxwhentheuserportalis
launchedorwhenauserlogsintoanapplicationoffloadedportal.ThisfeatureisenabledbydefaultwhenWeb
ApplicationFirewallislicensedandcanbedisabledfromtheWebApplicationFirewall>
Settingspage.
TheWebApplicationFirewall>Settingspagealsoallowstheadministratortoconfiguretheglobalidlesession
timeout.Itishighlyrecommendedthatthistimeoutvalueiskeptaslowaspossible.
HowareInsecureStorageandCommunications
Prevented?
InsecureCryptographicStorageandInsecureCommunicationsarepreventedbyencryptingkeysandpasswords
wherevernecessary,andbyusingSSLencryptiontoencryptdatabetweentheWebApplicationFirewallandthe
client.SonicWallSMAalsosupportsHTTPSwiththebackendwebserver.
HowisAccesstoRestrictedURLsPrevented?
SonicWallSMAsupportsaccesspoliciesbasedonhost,subnet,protocol,URLpath,andporttoallowordeny
accesstowebsites.Thesepoliciescanbeconfiguredgloballyorforusersandgroups.
HowareSlowlorisAttacksPrevented?
Slowlorisattackscanbepreventedifthereisanupstreamdevice,suchasaSonicWallSMAappliance,that
limits,buffers,orproxiesHTTPrequests.WebApplicationFirewallusesarate‐limitertothwartSlowlorisHT TP
DenialofServiceattacks.
NOTE:OnlytextorHTMLpages,andonlythefirst512KbytesareinspectedforcreditcardorSSN
disclosure.

SonicWallSecureMobileAccess8.6FeatureGuide
Overview
16
WhatTypeofPCIComplianceReportsAreAvailable?
PaymentCardIndustryDataSecurityStandard(PCIDSS)6.5(Version2.0)andPCIDSS6.6(Version1.2)are
coveredinPCIreporting.TheadministratorcanconfigureWebApplicationFirewalltosatisfythesePCI
requirements.
YoucangenerateanddownloadthePCIreportfileontheWebApplicationFirewall>Statuspage.
Two
tablesaredynamicallygeneratedinthePCIcompliancereporttodisplaythestatusofeachPCI
requirement.Theformatofthetableisshownintheexamplebelow:
ThefirstcolumndescribesthePCIrequirement.
ThesecondcolumndisplaysthestatusofthePCIrequirementundercurrentWebApplicationFirewallsettings.
Therearefourpossiblevaluesforthestatus,distinguishedbycolor.
• Satisfied(Green)
• PartiallySatisfied(Orange)
• Unsatisfied(Red)
• Unabletodetermine(Black)
Thethirdcolumnprovidescommentsanddetailsexplaining thestatusrating.IfthestatusisSatisfied,no
commentsareprovided.
HowDoesCookieTamperingProtectionWork?
TheSonicWallSecureMobileAccess/SRAapplianceprotectsimportantserver‐sidecookiesfromtampering.
Therearetwokindsofcookies:
Server‐SideCookies–Thesecookiesaregeneratedbybackendwebservers.Theyareimportantandhavetobe
protected.TheyhaveoptionalattributeslikePath,Domain,Secure,andHttpOnly.
Client
‐SideCookies–Thesecookiesarecreat edbyclientsidescriptsinuserbrowsers.Theyarenotsafe,and
canbeeasilytamperedwith.
NOTE:ThisisnotanofficialPCICompliancereport.Itisforyourself‐assessmentonly.

SonicWallSecureMobileAccess8.6FeatureGuide
Overview
17
ThisfeatureisfoundontheWebApplicationFirewall>Settingspage.
Thispagecontainsthefollowingoptions:
Portals–Alistofallapplicationoffloadingportals.Eachportalwillhaveitsownsetting.TheitemGlobalisthe
defaultsettingforallportals.
TamperProtectionMode–Threemodesareavailable:
• Disabled–Cookietamperprotectionisdisabled.
•Detectonly–Logthetamperedcookiesonly.
•Prevent–Stripallthetamperedcookiesandlogthem.
•InheritGlobal–Usetheglobalsettingforthisportal.ThisoptionisnotavailablewhenGlobalisselected
inthePortalsdrop‐downlist.
Encrypt
ServerCookies–Choosetoencryptnameandvalueseparately.Thisaffectsclient‐sidescriptbehavior
becauseitmakescookienamesorvaluesunreadable.Onlyserver‐sidecookiesareencryptedbytheseoptions.
CookieAttributes–Theat tributesHttpOnlyandSecureareappendedtoserver‐sidecookiesiftheyare
enabled.
TheattributeHttpOnlypreventstheclient‐sidescriptsfromaccessingthecookies,whichisimportantin
mitigatingattackssuchasCrossSiteScriptingandsessionhijacking.TheattributeSecureensuresthatthe
cookiesaretransportedonlyinHTTPSconnections.Bothtogetheraddastronglayerofsecurityforthe
server‐side
cookies.
ClientCookies–TheClientCookiesAllowoptionisenabledbydefault.InStrictmode,theAllowoptionis
disabled.Whendisabled,client‐sidecookiesarenotallowedtobesenttothebackendsystems.Thisoptiondoes
notaffectserver‐sidecookies.
ExclusionList–IftheExclusionList
isenabledandcontainsacookie,thecookieispassedasusualandisnot
protected.Youcanexcludeserver‐sidecookiesandclient‐sidecookies.
Exclusionlistitemsarecasesensitive,andintheformat‘CookieName@CookiePath’.Cookieswiththesame
nameanddifferentpathsaretreatedasdifferentcookies.‘CookiePath’
canbeleftemptytorepresentanypath.
NOTE:Bydefault,theattributeSecureisalwaysappendedtoanHT TPconnectionevenifCookie
TamperingProtectionisdisabled.Thisbehaviorisaconfigurableoption,andcanbeturnedoff.

SonicWallSecureMobileAccess8.6FeatureGuide
Overview
18
ImportGlobal–ApplicationOffloadingportalscanimporttheGlobalexclusionlist.
HowDoesApplicationProfilingWork?
TheadministratorcanconfigureapplicationprofilingontheWebApplicationFirewall>Rulespage.Application
profilingisperformedindependentlyforeachportal.
Afterselectingtheportal,youcanselectthetypeofapplicationcontentthatyouwanttoprofile.Youcan
chooseHTML/XML,Javascript,CSS,orAll,whichincludes
allcontenttypessuchasimages,HTML,andCSS.
HTML/XMLcontentisthemostimportantfromasecuritystandpoint,becauseittypicallycoversthemore
sensitivewebtransactions.Thiscontenttypeisselectedbydefault.
ThentheSonicWallSMAapplianceisplacedinlearningmodebyclickingontheBeginProfiling
button(the
buttonthenchangestoEndProfiling).Theprofilingshould bedonewhiletrustedusersareusingapplications
inanappropriateway.TheSMArecordsinputsandstoresthemasURLprofiles.TheURLprofilesareliste dasa
treestructureontheWebApplicationFirewall>Rulespage
intheApplicationProfilingsection.
OnlytheURLspresentedashyperlinksareaccessibleURLsonthebackendserver.Youcanclickonthehyperlink
toeditthelearnedvaluesforthatURLif thevaluesarenotaccurate.Youcanthengeneraterulestousethe
modifiedURLprofile.
TheSMA
learnsthefollowingHTTPParameters:
• ResponseStatusCode
• PostDataLength–ThePostDataLengthisestimatedbylearningthevalueintheContent‐Lengthheader.
Themaximumsizeissettothepoweroftwothatisclosesttoandhigherthanthisvalue.This
accommodatestheamountof
memorythatmayhavebeenallocatedbythebackendapplication.For
example,foraContentLengthof65,thenextpoweroftwogreaterthan65is128.Thisisthelimit
configuredintheURLprofile.Iftheadministratordeterminesthatthisisnotaccurate,thevaluecanbe
modifiedappropriately.
• RequestParameters–ThisisthelistofparametersthataparticularURLcanaccept.
NOTE:Contenttypescanbesavedforapplicationscurrentlybeingprofiled.

SonicWallSecureMobileAccess8.6FeatureGuide
Overview
19
Whenanadequateamountofinputhasbeenlearned,youcanclicktheEndProfi lingbuttonandarereadyto
generatetherulesfromthelearnedinput.Youcansetoneofthefollowingasadefaultactionforthegenerated
rulechains:
• Disabled–Thegeneratedruleswillbedisabled
ratherthanactive.
• DetectOnly–Contenttriggeringthegeneratedrulewillbedetectedandlogged.
• Prevent–Contenttriggeringthegeneratedrulewillbeblockedandlogged.
IfarulechainhasalreadybeengeneratedfromaURLprofileinthepast,thentherulechainwillbeoverwritten
only
ifOverwriteexistingRuleChainsforURLProfi lesisselected.WhenyouclicktheGenerateRules
button,therulesaregeneratedfromtheURLprofiles.IfaURLprofilehasbeenmodified,thosechangesare
incorporated.
HowDoesRateLimitingforCustomRulesWork?
TheadministratorcanconfigureratelimitingwhenaddingoreditingarulechainfromtheWebApplication
Firewall>Rulespage.Whenratelimitingisenabledforarulechain,theactionfortherulechainistriggered
onlywhenthenumberofmatcheswithinaconfiguredtimeperiodisabove
theconfiguredthreshold.
ThistypeofprotectionisusefulinpreventingBruteForceandDictionaryattacks.Anexamplerulechainwitha
RuleChainIDof15002isavailableinthemanagementinterfaceforadministratorstouseasreference.
TheassociatedfieldsareexposedwhenEnableHitCountersisselectedat
thebottomoftheNewRuleChain
orEditRuleChainscreen.
Oncearulechainismatched,WebApplicationFirewallkeepsaninternalcountertotrackhowmanytimesthe
rulechainismatched.TheMaxAllowedHitsfieldcontainsthenumberofmatchesthatmustoccurbeforethe
rule
chainactionistriggered.IftherulechainisnotmatchedforthenumberofsecondsconfiguredintheReset
HitCounterPe riodfield,thenthecounterisresettozero.
RatelimitingcanbeenforcedperremoteIPaddressorperusersessionorboth.TrackPerRemot eAddress
enables
ratelimitingbasedontheattacker’sremoteIPaddress.
TrackPer Sessionenablesratelimitingbasedontheattacker’sbrowsersession.Thismethodsetsacookiefor
eachbrowsersession.TrackingbyusersessionisnotaseffectiveastrackingbyremoteIPiftheattackerinitiates
anewuser
sessionforeachattack.
TheTrackPerRemo teAddressoptionusestheremoteaddressasseenbytheSMA/SRAappliance.Inthecase
wheretheattackusesmultipleclientsfrombehindafirewallthatisconfiguredwithNAT,thedifferentclients
effectivelysendpack etswiththesamesourceIPaddressand
willbecountedtogether.

SonicWallSecureMobileAccess8.6FeatureGuide
Overview
20
SupportedPlatforms
WebApplicationFirewallisavailableonthefollowingSMA/SRAappliances:
• SMA200
• SMA400
• SRA1600
• SRA4600
• SMA500vVirtualAppliance
NOTE:ApplicationprofilingissupportedonlyontheSMA400,SRA4600,andSMA500vVirtualAppliance.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
4
21
ConfiguringWebApplicationFirewall
ToconfiguretheWebApplicationFirewallfeature,seethefollowingsections:
• ViewingandUpdatingWebApplicationFirewallStatusonpage21
• ConfiguringWebApplicationFirewallSettingsonpage23
• ConfiguringWebApplicationFirewallSignatureActionsonpage32
• DeterminingtheHostEntryforExclusionsonpage36
• ConfiguringCustomRulesandApplication
Profilingonpage38
• UsingWebApplicationFirewallMonitoringonpage55
• UsingWebApplicationFirewallLogsonpage62
WebApplicationFirewallisoftenusedtoprotectanApplicationOffloadingportal.ConfiguringanApplication
OffloadingPortalonpage65summarizeshowtoconfigureanApplicationOffloadingportal.SeetheSonicWall
SMAApplicationOffloadingandHT TP(S)BookmarksFeatureGuideortheSMA8.6AdministrationGuidefor
moredetailedinformation.
ViewingandUpdatingWebApplication
FirewallStatus
TheWebApplicationFirewall>StatuspageprovidesstatusinformationabouttheWebApplicationFirewall
signaturedatabaseanddisplaysthelicensestatusandexpirationdate.TheSynchronizebuttonallowsyouto
downloadthelatestsignaturesfromtheSonicWallonlinedatabase.YoucanusetheDownloadbuttonto
generateanddownloada
PCIcompliancereportfile.
NOTE:WebApplicationFirewallrequiresthepurchaseofanadditionallicense.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
22
ViewingStatusandSynchronizingSignatures
ToviewthestatusofthesignaturedatabaseandWebApplicationFirewallservicelicense,andsynchronizethe
signaturedatabase,performthefollowingstepsintheappliancemanagementinterface:
1NavigatetoWebApplicationFirewall>Status.TheWAFStatussectiondisplaysthefollowing
information:
• Statusofupdatestothesignaturedatabase
• Timestamp
ofthesignaturedatabase
• Timethatthesystemlastcheckedforavailableupdatestothesignaturedatabase
• ExpirationdateoftheWebApplicationFirewallsubscriptionservice
• Statusofthe WebApplicationFirewalllicense
2Ifupdatesareavailableforthesignaturedatabase,theApplybuttonisdisplayed.ClickApplyto
download
theupdates.
YoucanselectanoptiontoupdateandapplynewsignaturesautomaticallyontheWebApplication
Firewall>Settingspage.Ifthisautomaticupdateoptionisenabled,theApplybuttondisappearsfrom
theWebApplicationFirewall>Statuspageassoonasthenewsignaturesareautomaticallyapplied.
3Tosynchronize
thesignaturedatabasewiththeSonicWallonlinedatabaseserver,clickSynchronize.The
timestampisupdated.
DownloadingaPCIComplianceReport
TodownloadaPCIDSS6.5/6.6compliancereport:
1NavigatetoWebApplicationFirewall>Status.
2 ClicktheDownloadbutton.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
23
3IntheFileDownloaddialogbox,clickOpentocreatethePCIreportasatemporaryfileandviewitwith
AdobeAcrobat,orclickSavetosavethereportasaPDFfile.
ConfiguringWebApplicationF irewallSettings
TheWebApplicationFirewall>SettingspageallowsyoutoenableanddisableWebApplicationFirewallon
yourSonicWallSMA/SRAappliancegloballyandbyattackpri ority.Youcanindividuallyspecifydetectionor
preventionforthreeattackclasses:high,medium,andlowpriorityattacks.
Thispagealsoprovidesconfigurationoptionsforother
WebApplicationFirewallsettings.Thefollowingsections
describetheproceduresforenablingandconfiguringWebApplicationFirewallsettings:

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
24
• EnablingWebApplicationFirewallandConfiguringGeneralSettingsonpage24
• ConfiguringGlobal Exclusionsonpage25
• ConfiguringIntrusionPreventionErrorPageSettingsonpage26
• ConfiguringCross‐SiteRequestForgeryProtectionSettingsonpage27
• ConfiguringCookieTampering P rotectionSettingsonpage28
• ConfiguringWebSiteCloakingonpage
30
• ConfiguringInformationDisclosureProtectiononpage30
• ConfiguringSessionManagementSettingsonpage32
EnablingWebApplicationFirewallandConfiguring
GeneralSettings
ToenableandactivateWebApplicationFirewall,youmustselectthecheckboxtogloballyenableitandselectat
leastoneofthecheckboxesintheSignatureGroupstable.ThesettingsintheGeneralSettingssectiononthis
pageallowyoutogloballymanageyournetworkprotectionagainstattacksbyselec ting
thelevelofprotection
forhigh,medium,orlowpriorityattacks.YoucanalsocleartheglobalEn ableWebApplicationFirewall
checkboxtotemporarilydisableWebApplicationFirewallwithoutlosinganyofyourcustomconfiguration
settings.
YoucanenableautomaticsignatureupdatesintheGeneralSettingssection,sothatnewsignatures
are
automaticallydownloadedandappliedwhenavailable.Alogentryisgeneratedforeachautomaticsignature
update.Ifasignatureisdeletedduringautomaticupdating, itsassociatedExclusionListisalsoremoved.Alog
entryisgeneratedtorecordtheremoval.YoucanviewthelogentriesontheWeb
ApplicationFirewall>Logs
page.
ToconfigureglobalsettingsforWebApplicationFi rewall:
1OntheWebApplicationFirewall>Settingspage,expandtheGeneralSettingssection.
2 SelectEnableWebApplicationFirewall.
3AwarningdialogboxisdisplayedifnoneofthesignaturegroupshavePreventAllalreadyselected.Click
OKinthedialogboxtosetallsignaturegroupstoPreventAll,orclick
Canceltoleavethesettingsasthey
areortomanuallycontinuetheconfiguration.
4 SelectApplySignatureUpdatesAutomaticallytoenablenewsignaturestobeautomatically
downloadedandappliedwhenavailable.YoudonothavetoclicktheApplybuttonontheWeb
ApplicationFirewall>Statuspagetoapplythe
newsignatures.
5 SelectthedesiredlevelofprotectionforHighPriorityAttacksintheSignatureGroupstable.Selectone
ofthefollowingoptions:
• SelectPreventAlltoblockaccesstoaresourcewhenanattackisdetected.SelectingPreventAll
automaticallyselectsDetectAll,turningonlogging.
• ClearPreventAll
andselectDetectAlltologattackswhileallowingaccesstotheresource.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
25
• Togloballydisableallloggingandpreventionforthisattackprioritylevel,clearbothcheckboxes.
6 SelectthedesiredlevelofprotectionforMediumPriorityAttacksintheSignatureGroupstable.
7 SelectthedesiredlevelofprotectionforLowPriorityA ttacksintheSignatureGroupstable.
8Whenfinished,clickAccept.
9 ClickOK
intheconfirmationdialogifitisdisplayed.
ConfiguringGlobalExclusions
TherearethreewaysthatyoucanexcludecertainhostsfromcurrentlyconfiguredglobalWebApplication
Firewallsettings.YoucancompletelydisableWebApplicationFirewallforcertainhosts,youcanlowerthe
actionlevelfromPreventtoDetectforcertainhosts,oryoucansetWebApplicationFirewalltotak eno
action.
TheaffectedhostsmustmatchthehostnamesusedinyourHTTP(S)bookmarksandCitrixbookmarks,andthe
VirtualHostDomainNameconfiguredforanoffloadedwebapplication.
Toconfigureglobalexclusions:
1OntheWebApplicationFirewall>Settingspage,expandtheGeneralSettingssection.
2 ClickGlobalExclusions.
3IntheEditGlobalExclusionspage,theactionyousetoverridesthesignaturegroupsettingsforthe
resourcesconfiguredonthesehostpages.SelectoneofthefollowingfromtheActiondrop‐downlist:
• Disable–
DisablesWebApplicationFirewallinspectionforthehost.
•Detect–Lowerstheactionlevelfrompreventiontoonlydetectionandloggingforthehost.
•NoAction–WebAppli cationFirewallinspectshosttraffic,buttakesnoaction.
4IntheHostfield,typethehostentryasitappearsinthebookmarkor
offloadedapplication.Thiscanbea
hostnameorIPaddress.Upto32charactersareallowed.Todeterminethecorrecthostentryforthis

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
26
exclusion,seeDeterminingtheHostEntryforExclusionsonpage36.
Youcanconfigureapathtoaparticularfolderorfilealongwiththehost.Theprotocol,port,andthe
requestparametersaresimplyignoredintheURL.Ifapathisconfigured,thentheexclusionisrecursively
appliedto
allsubfoldersandfiles.Forinstance,ifHostissettowebmai l.com pany. com /exchange,then
allfilesandfoldersunderexchan ge arealsoexcluded.
5 ClickADDtomovethehostnameintothelistbox.
6RepeatStep4andStep5toaddmorehoststothisexclusion.
7Whenfinished,clickAccept.
ConfiguringIntrusionPreventionErrorPageSettings
Toconfiguretheerrorpagetousewhenintrusionsaredetected:
1ExpandtheIntrusionPreventionErrorPageSettingssection.
2IntheIntrusionPreventionResponsedrop‐downlist,selectthetypeoferrorpagetobedisplayedwhen
blockinganintrusionattempt.
3Tocreateacustompage,selectCustomIntrusionPreventionPageandmodifythesampleHTMLinthe
textbox.
4Toviewthe
resultingpage,clickthePreviewbutton.
5Toresetthecurrentcustomizederrorpagetothedefaulterrorpage,clicktheDefaultBlockedPage
buttonandthenclickOKintheconfirmationdialogbox.
6Ifyoudonotwanttouseacustomizederrorpage,selectoneofthefollowingforthe
errorpage:
• HTTPErrorCode400BadRequest

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
27
• HTTPErrorCode403Forbidden
• HTTPErrorCode404NotFound
• HTTPErrorCode500InternalServerError
7Whenfinished,clickAccept.
ConfiguringCross‐SiteRequestForgeryProtection
Settings
Cross‐SiteRequestForgeryprotectionisconfiguredindependentlyforeachApplicationOffloadingportal.New
withthisreleaseistheFormbasedProtectionMethod,whichprovidesaseamlesssolutionandresultsinless
falsepositives.Optionallywhenupgradingfromapreviousrelease,youcankeeptheoriginalProtection
Method,URLRewrite‐based
ProtectionMethod.
WhenaCSRFattackisdetected,logentriesarecreatedinboththeWebApplicationFirewall>LogsandLogs>
Viewpages.FormoreinformationaboutCSRF/XSRFattacks,seeHowisCross‐SiteRequestForgeryPrevented?
onpage14.
ToconfigurethesettingsforCSRFprotectionwiththeForm‐basedProtectionMethod:
1ExpandtheCross‐SiteRequestForgery(C SRF/XSRF)Protectionsection.
2InthePortalsdropdownlist,selectthePortaltowhich theseCSRFprotectionsettingswillapply.To
maketheseCSRFsettingsthedefaultforallportals,selectGlobal.
3 SelectForm‐basedProtectionfromtheProtectionMethoddropdownlist.
4ForContent
Types,selectthetypesofcontentyouwanttobeprofiledbyCSRF.YoucanselectAll,
HTML/XML,Javascript,orCSS.
5 ClicktheBeginProfilingbuttontostarttheCSRFForm‐basedProtection.Ifyouwishtostopprofiling,
clickEndProfi ling.
6Whenfinished,clickAccept.
NOTE:IfyouareupgradingfromapreviousfirmwareversionandswitchtheProtectionMethodto
Form ‐basedProtection,thecontrolsmayappeargrayedanddisabled.SimplyclicktheA cceptbuttonto
activatethecontrols.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
28
ToconfigurethesettingsforCSRFprotectionwithURLRewrite‐basedProtectionMethod:
1ExpandtheCross‐SiteRequestForgery(C SRF/XSRF)Protectionsection.
2InthePortalsdrop‐downlist,selecttheApplicationOffloadingportaltowhichtheseCSRFprotection
settingswillapply.TomaketheseCSRFsettingsthedefaultforallportals,selectGlobal.
3 SelectURLRewrite‐basedProtectionfromtheProtectionMethoddropdown
list.
4ForProtectionMode ,selectthedesiredlevelofprotectionagainstCSRFattacks.YoucanselectDetect
Onlytologtheseattacks,orPrev enttologandblockthem.SelectDisabledtodisableCSRFprotection
ontheportal.
5Whenfinished,clickAccept.
ConfiguringCookieTamperingProtectionSettings
CookietamperingprotectionisconfiguredindependentlyforeachApplicationOffloadingportal.
Toconfigurethesettingsforcookietamperingprotection:
1ExpandtheCookieTamperingProtectionsection.
2InthePortalsdrop‐downlist,selecttheApplicationOffloadingportaltowhichthesecookietampering
protectionsettingswillapply.Tomakethesecookietamperingsettingsthedefaultforallportals,select
Global.
3ForTamperProtectionMode,selectthedesiredlevelofprotectionagainstcookie
tampering.Youcan
selectDetectOnlytologtheseattacks,orPreventtologandblockthem.SelectDisabledtodisable
cookietamperingprotectionontheportal.
4ForEncryptServerCookies,selectNametoencryptcookienames,and/orselectValuetoencryptcookie
values.Thisaffectsclient‐sidescriptbehavior
becauseitmakescookienamesorvaluesunreadable.Only
server‐sidecookiesareencrypte dbytheseoptions.
5ForCookieAttributes,selectHttpOnlytoappendtheHttpOnlyattributetoserver‐sidecookies,and/or
selectSecuretoappendtheSecureattributetoserver‐sidecookies.TheattributeHttpOnlypreventsthe

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
29
client‐sidescriptsfromaccessingthecookies,whichisimportantinmitigatingattackssuchasCrossSite
Scriptingandsessionhijacking.TheattributeSecureensuresthatthecookiesaretransportedonlyin
HTTPSconnections.Bothtogetheraddastronglayerofsecurityfortheserver‐sidecookies.
6ForClientCookies,select
Allowifanapplicationontheportalneedsalloftheclientcookies.When
disabled,client‐sidecookiesarenotallowedtobesenttothebackendsystems.Thisoptiondoesnot
affectserver‐sidecookies.
7FortheExclusionList,selectEnabledtodisplayadditionalfieldsforconfiguration.
8Toentera
customcookienameandpathtotheExclusionList,clickintheCookieNamefieldtotypein
thenameofthecookie,andclickintheCookiePathfieldtotypeinthepath.ThenclicktheAdd>
button.
9Toaddoneormorealready‐detectedcookiesto
theExclusionList,selectthedesiredcookiesinthe
DetectedCookieslist,holdingtheCtrlkeywhil eclickingmultiplecookies,andthenclickthe<Add
buttontoaddthemtotheExclusionList.
10 ToremovecookiesfromtheExclusionList,selectthecookiestoberemovedandthenclick
theRemove
button.
11 TocleartheDetectedCookieslist,clickthe Clearbutton.
12 Whenfinished,clickAccept.
ConfiguringWebSiteCloaking
UnderWebSiteCloaking ,youcanfilteroutheadersinresponsemessagesthatcouldprovideinformationto
clientsaboutthebackendwebserver,whichcouldpossiblybeusedtofindavulnerability.
Toconfigurewebsitecloaking:
1ExpandtheWebSiteCloakingsection.
2IntheBlockResponseHeaderfields,typetheserverhostnameintothefirstfieldandtypetheheader
nameintothesecondfield,thenclickAdd.
Forexample,ifyousetthehostnameto“webmail.xyz.com”andtheheadernameto“X‐OWA‐version”,
headerswiththename“X‐OWA‐ver sion”fromhost“webmail.xyz.com”willbeblocked.Ingeneral,listed

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
30
headerswillnotbesenttotheclientifanHTTP/HTTPSbookmarkoroffloadedapplicationisusedto
accessalistedwebserver.
Toblockacertainheaderfromallhosts,setthehostnametoanasterisk(*).Youcanaddupto64
host/headerpairs.IntheHTTP
protocol,responseheadersarenotcasesensitive.
3Toremoveahost/headerpairfromthelisttobeblocked,selectthepairinthete xtboxandthenclickthe
Removebutton.
4Whenfinished,clickAccept.
ConfiguringInformationDisclosureProtection
UnderInformationDisclosureProtection,youcanprotectagainstinadvertentdisclosureofcreditcardand
SocialSecuritynumbers(SSN)inHTMLwebpage s.Youcanalsoenterconfidentialtextstringsthatshouldnotbe
revealedonanywebsiteprotectedbyWebApplicationFirewall.
Toconfigureinformationdisclosureprotection:
1ExpandtheInformationDisclosureProtectionsection.Thetablecontainsarowforeachpossible
patternorrepresentationofasocialsecuritynumberorcreditcardnumberthatWebApplication
FirewallcandetectintheHTMLresponse.
2 SelectEnableCreditCard/SSNProtection.
3IntheMaskCharacterdrop‐downlist,selectthecharacter
tobesubstitutedwhenmaskingtheSSNor
creditcardnumber.
4Inthetable,selectthelevelofprotectiondesiredforeachrepresentationofaSSNorcreditcardnumber.
Youcanselectoneofthefollowingineachrow:
NOTE:BlockingwillnotoccurforheaderssuchasContent‐TypethatarecriticaltotheHTTP
protocol.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
31
• Disabled–Donotmatchnumbersinthisformat.Nologgingormaskingisperformed.
•Detect–Detectnumbersinthisformatandcreatealogentrywhendetected.
•MaskPartially–Substitutethemaskingcharacterforthealldigitsinthenumber,exceptthelast
fewdigitssuchthattheconfidentiality
ofthenumberisstillpreserved.
•MaskFully–Substitutethemaskingcharacterforalldigitsinthenumber.
•Block–Donottransmitordisplaythenumberatall,eveninmaskedformat.
5Belowthetable,intheBlocksensitiveinformationwithinHTMLpagestextbox,typeconfidentialtext
stringsthat
shouldnotberevealedonanywebsiteprotectedbyWebApplicationFirewall.Thistextis
casein sensitive,canincludeanynumberofspacesbetweenthewords,butcannotincludewildcard
characters.Addnewphrasesonseparatelines.EachlineispatternmatchedwithinanyHTMLresponse.
6Whenfinished,clickAccept
.
ConfiguringSessionManagementSettings
UnderSessionManagement,youcancontrolwhetherthelogoutdialogwindowisdisplayedwhenauserlogs
intotheuserportalorintoanapplicationoffloadedportal.Youcanalsosettheinactivitytimeoutforusersin
thissection.
Toconfiguresessionmanagementsettings:
1ExpandtheSessionManagementsection.
2 SelectLaunchLogoutDialogWindowafterLogintodisplaythesessionlogoutpopupdialogboxwhen
theuserportalislaunchedorwhenauserlogsintoanapplicationoffloadedportal.
3IntheGlobalInactivityTimeoutfield,typethenumberofinactiveminutesallowedbeforethe
useris
loggedout.ThissettingcanbeoverriddenbyGrouporUsersettings.
4Whenfinished,clickAccept.
NOTE:TomitigateCSRFattacks,itisimportanttokeepalowidletimeout valueforusersessions,
suchas10minutes.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
32
ConfiguringWebApplicationFirewallSignature
Actions
TheWebApplicationFirewall>Signaturespageallowsyoutoconfigurecustomhandlingorexclusionofcertain
hostsonaper‐signaturebasis.Youcanusesignature‐basedexclusionstoapplyexclusionsforallhostsforeach
signature.
Youcanalsorevertbacktousingtheglobalsettingsforthesignature
grouptowhichthissignaturebelongs
withoutlosingtheconfigurationdetailsofexistingexclusions.
Signatureslistedonthispagecanbedividedintopages(defaultis50signaturesperpage)andfilteredby
searchingforakeyword.Todisplayonlysignaturescontainingakeywordinallfieldsora
specificfield,typethe
keywordintheSearchfield,selectAllFieldsoraspecificfieldtosearch,andclickSearch.Allmatchesare
highlighted.Or,clickExcludetodisplayonlysignaturesthatdonotcontainthekeyword.ClickRes et todisplay
allsignatures.Inaddition,thelist
canbesortedbythecontentsofanycolumninascendingordescendingorder
byclickingthecolumnheading.
OntheSettingspage,globalsettingsmustbesettoeitherPreventAllorDetectAllfortheSignatureGroupto
whichthespecificsignaturebelongs.Ifneitherisset,thatSignature
Groupisgloballydisabledandcannotbe
modifiedonaper‐signaturebasis.SeeEnablingWebApplicationFirewallandConfiguringGeneralSettingson
page24.
Seethefollowingsections:
• EnablingPerformanceOptimizationonpage33
• ConfiguringSignatureBasedCustomHandlingandExclusionsonpage34
• RevertingaSignaturetoGlobal
Settingsonpage35

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
33
• RemovingaHostfromaPer‐SignatureExclusiononpage36
EnablingPerformanceOptimization
ThePerformanceOptimizationoptionallowsyoutodisablesomerelativelylessseveresignaturesthat
significantlyaffecttheperformanceofcertainwebapplications.ThesesignaturesareidentifiedbytheSonicWall
signatureteamandthelistispushedouttoSonicWallSMA/SRAappliances.WhenyouselectEnable
Performan ce Opti miza tion,thesesignaturesare
disabledforWebApplicationFirewall.
TheWebApplicationFirewall>Signaturespageindicatesthedisabledsignaturesbydisplayingthemingray,as
showninEnabling PerformanceOptimization.
EnablingPerformanceOptimization
ConfiguringSignatureBasedCustomHandlingand
Exclusions
Youcandisableinspectionforasignatureintraffictoanindividualhost,orforallhosts.Youcanalsochangethe
handlingofdetectedthreatsforanindividualhostorforallhosts.Ifthesignaturegrouptowhichthesignature
belongsissetgloballytoDetectAll,youcan
raisethelevelofprotectiontoPreventfortheconfiguredhosts.If
nohostsareconfigured,theactionisappliedtothesignatureitselfandactsasaglobalsettingforallhosts.This
changewillblockaccesstoahostwhentheattacksignatureisdetected.Similarly,youcan
lowerthelevelof
protectiontoDetectiftheassociatedsignaturegroupisgloballysettoPreventAll.
NOTE:Forsignaturebasedcustomizationtotakeeffect,thesignaturegroupofthemodifiedsignature
mustbegloballyenabledforeitherpreventionordetectionontheWebApplicationFirewall>Settings
page.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
34
Toconfigureoneormorehostswithanexclusionfrominspectionforasignature,ortoconfigure
customhandlingwhenWebApplicationFirewalldetectsaspecificsignatureforoneormorehosts,:
1OntheWebApplicationFirewall>Signaturespage,clicktheConfigurebuttonforthesignature
thatyouwishtochange.TheEditWAFSignature‐basedExclusionsscreendisplays.
2IntheEditWAFSignature‐basedExclusionsscreen,selectoneofthefollowingactionsfromtheAction
drop‐downlist:
•DISABLE–Disable
WebApplicationFirewallinspectionsforthissignatureintrafficfromhosts
listedinthisex clusion
•DETECT–Detectandlogthreatsmatchingthissignaturefromhostslistedinthisexclusion,butdo
notblockaccesstothehost
•PREVENT–Logandblockhostaccessforthreatsmatchingthissignaturefromhosts
listedinthis
exclusion
•INHERITGLOBAL‐UsetheglobalsignatureexclusionlistconfiguredontheWebApplication
Firewall>Settingspage.
3Toapplythisactiongloballytoallhosts,leavetheHostfieldblank.Toapplythisactiontoanindividual
host,typethehostentryasitappearsinthe
bookmarkoroffloadedapplicationintotheHostfield.This
canbeahostnameoranIPaddress.Todeterminethecorrecthostentryforthisexclusion,see
DeterminingtheHostEntryforExclusionsonpage36.
Youcanconfigureapathtoaparticularfolderorfilealongwiththe
host.Theprotocol,port,andthe
requestparametersaresimplyignoredintheURL.Ifapathisconfigured,thentheexclusionisrecursively
appliedtoallsubfoldersandfiles.Forinstance,ifHostissettowebmai l.sonicwall.com/exchange,then
allfilesandfoldersunderexchan ge arealsoexcluded.
4Ifyou
specifiedahost,clickAddtomovethehostnameintothelistbox.
5Ifyouwanttoapplythisactiontoadditionalindividualhosts,repeatStep3andStep4toaddmorehosts
tothisexclusion.
6 ClickAccept.IftheHostlistcontainshostentries.TheSonicWallSMA/SRAappliance
verifiesthateach
hostentryisvalid.Ifnohostswerespecified,adialogboxconfirmsthatthisisaglobalactiontobe
appliedtothesignatureitself.
7 ClickOKintheconfirmationdialogbox.
8 ClickAcceptontheWebApplicationFirewall>Signaturespagetoapplytheupdatedsettings.New
settingsareappliedtoanynewHTTPconnectionsandrequests.TheexistingHTTPconnectionsand
requestscontinuetousetheoldsettingsuntiltheyareterminated.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
35
RevertingaSignaturetoGlobalSettings
Youcanreverttousingglobalsignaturegroupsettingsforasignaturethatwaspreviouslyconfiguredwith an
exclusion,withoutlosingtheconfiguration.Thisallowsyoutoleavethehostnamesinplaceincaseyouneedto
re‐enabletheexclusion.
Toreverttousingglobalsignaturegroupsettingsforasignature:
1OntheWebApplicationFirewall>Signaturespage,clicktheConfigurebuttonforthesignature
thatyouwishtochange.
2IntheEditWAFSignature‐basedExclusionsscreen,selectINHERITGLOBALfromtheActiondrop‐down
list.
3TheHostfieldmaybeblankifglobalsettingswerepreviouslyappliedtothissignature.
Toreverttoglobal
signaturesettingsforallhosts,leavetheHostfieldblank.Toapplythisaction tooneormoreindividual
hosts,leavethesehostentriesintheHostfieldandremoveanyhostentriesthatarenottobereverted.
4 ClickAccept.TheSonicWallSMA/SRAapplianceverifies
thateachhostentryisvalid.
5 ClickOKintheconfirmationdialogbox.
6 ClickAcceptontheWebApplicationFirewall>Signaturespagetoapplytheupdatedsettings.New
settingsareappliedtoanynewHTTPconnectionsandrequests.TheexistingHTTPconnectionsand
requestswillcontinuetousetheoldsettings
untiltheyareterminated.
RemovingaHostfromaPer‐SignatureExclusion
Toremoveahostfromaconfiguredexclusionforasignature:
1OntheWebApplicationFirewall>Signaturespage,clickConfigureforthesignaturethatyouwish
tochange.
2 SelectthehostentryinthelistboxundertheHostfield,andthenclickRemove.
3RepeatStep2toremoveotherlistedhosts,ifdesired.
4 ClickAccept.TheSonicWallSMA/SRAapplianceverifies
thateachhostentryisvalid.
5 ClickOKintheconfirmationdialogbox.
6 ClickAcceptontheWebApplicationFirewall>Signaturespagetoapplytheupdatedsettings.New
settingsareappliedtoanynewHTTPconnectionsandrequests.TheexistingHTTPconnectionsand
requestswillcontinuetousetheoldsettings
untiltheyareterminated.
DeterminingtheHostEntryforExclusions
Whenconfiguringanexclusion,eithergloballyorper‐signature,youmustprovidethehostnameorIPaddress.
TheaffectedhostsmustmatchthehostnamesusedinyourHTTP(S)bookmarksandCitrixbookmarks,andthe
virtualhostdomainnameconfiguredforanoffloadedwebapplication.
Foradescriptionofhow
todeterminethecorrecthostname,seethefollowingsections:
• ViewingtheHostEntryinaBookmarkonpage36
• ViewingtheHostEntryinanOffloadedApplicationonpage37

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
36
ViewingtheHostEntryinaBookmark
Youcandetermineexactlywhathostnametoenterinyourexclusionbyviewingtheconfigurationdetailsofthe
bookmark.
Toviewthehostentryinabookmark:
1NavigatetotheVirtualOfficepage,andclickShowEditControlsabovethelistofbookmarks.
2 ClicktheEditbuttonforthebookmark.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
37
3IntheEditBookmarkscreen,viewthehostentryintheNameorIPAddressfield.
4 ClickCancel.
ViewingtheHostEntryinanOffloadedApplication
Youcandetermineexactlywhathostnametoenterinyourexclusionbyviewingtheconfigurationdetailsofthe
offloadedapplication.Inanoffloadedapplication,youwillusethevirtualhostdomainname.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
38
Toviewthevirtualhostdomainnameinanoffloadedapplication:
1NavigatetothePortals>PortalspageandclickConfigurenexttotheoffloadedapplication.
2IntheEditPortalscreen,clicktheVirtualHosttab.
3ViewthehostentryforyourexclusionintheVirtualHostDomainNamefield.
4 ClickCancel.
ConfiguringCustomRulesandApplication
Profiling
TheWebApplicationFirewall>Rulespageallowsyoutoconfigurecustomrulesandapplicationprofiling.
Applicationprofilingallowsyoutogeneratecustomrulesinanautomatedmannerbasedonatrustedsetof
inputsusedtodevelopaprofileofwhatinputsareacceptablebyanapplication.Otherinputsare
denied,
providingpositivesecurityenforcement.WhenyouplacetheSonicWallSMA/SRAapplianceinlearningmodein
astagingenvironment,itlearnsvalidinputsforeachURLaccessedbythetrustedusers.Atanypointduringor
afterthelearningprocess,customrulescanbegeneratedbasedonthe“learned”profiles.For
moreinformation
aboutapplicationprofilin g,seetheHowDoesApplicationProfilingWork?onpage18.
NOTE:ApplicationprofilingissupportedonlyontheSonicWallSMA400,SRA4600,andtheSonicWall
SMA500vVirtualAppliance.
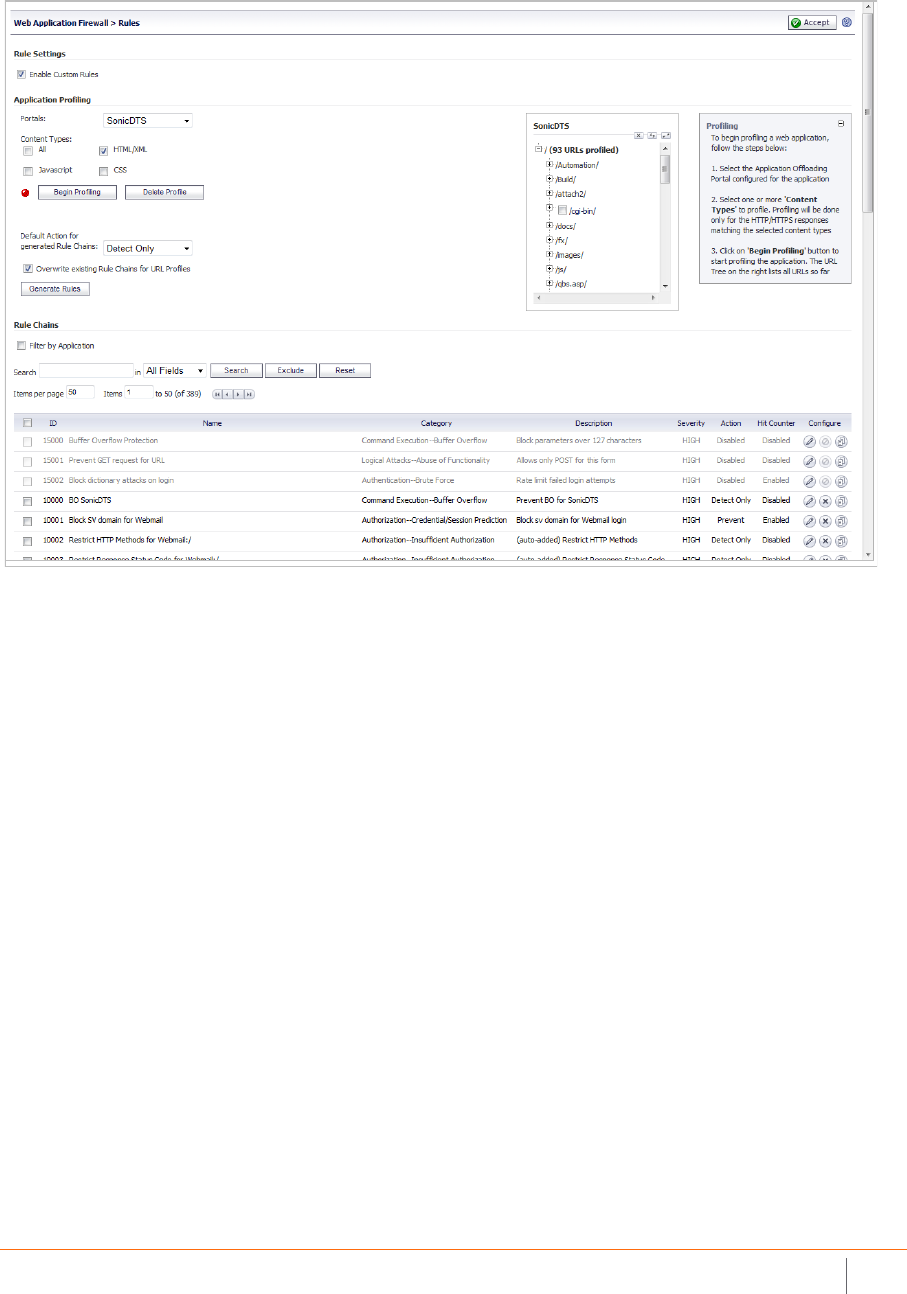
SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
39
CustomrulescreatedonthispagehaveallthesamepropertiesasthesignaturesthatSonicWallpushesoutto
WebApplicationFirewall‐enabledappliances.
WebApplicationFirewall>RulesPage
Toadd arulemanually,youcreatearulechainandthenaddruleswithinit.Arulechainisa
collectionof
rulesandincludesadditi o n alattributessuchastheseverityrati ng,name,descriptio n,hitcountersforra te
limiting ,andtheactiontotakewhentherulechainmatchessometraffic.
RuleslistedontheRulespagecanbedividedintopages(defaultis50rulesperpage)andfilteredby
searching
forakeyword.Todisplayonlyrulescontainingakeywor dinallfieldsoraspecificfield,typethekeywordinthe
Searchfield,selectAllFieldsoraspecificfieldtosearch,andclickSearch.Allmatchesarehighlighted.Or,click
Excludetodisplayonly
rulesthatdonotcontainthekeyword.ClickRes e ttodisplayallrules.
Rulechainsgeneratedbyapplicationprofilescanbefilteredbyapplication.SelecttheFilterbyApplication
checkboxtofilterrulechains.
Toaddarulemanually,youcreatearulechainandthenaddruleswithinit.
Arulechaincontainsacollectionof
rules,andincludesadditionalattributessuchastheseverityrating,name,description,hitcountersforrate
limiting,andtheactiontotakewhentherulechainmatchessometraffic.
Forexample,customrulesandrulechainscanbeusedtodistinguishbetweenlegitimateand
illegitimatetraffic
asdefinedbyawebapplicationthatisusingacertainURIorrunningonacertainportal.Oneruleinthechainis
configuredtomatchtheURIorportalhostname,whileanotherruleiscreatedthatmatchesanundesirable
valueforanotherelementofthe
HTTP(S)traffic.Whentherulechain(bothrules)matchessometraffic,the
configuredaction isperformedtoblockorlogthebadtrafficfromthatURIorportal.Whentherequestis
blocked,theuserseesacustomblockpagesuchasthatinBlockPage.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
40
BlockPage
TheWebApplicationFirewall>Monitoringpagealsoshowstheactivityinthegraphs.MonitoringPageAfter
Blockingshowsdetectedandpreventedthreatsduringa30dayperiod.Formoreinformationaboutthe
Monitoringpage,seeUsingWebApplicationFirewallMonitoringonpage55.
MonitoringPageAfterBlocking
Rules
arematchedagainstbothinboundandoutboundHTTP(S)traffic.Whenallrulesinarulechainfinda
match,theactiondefinedintherulechainisperformed.Youcanalsoenableratelimitinginrulechainsto
triggeranactiononlyafterthenumberofmatchingattacksexceedsa
thresholdwithinacertaintimeperiod.
Youcanconfiguretheactiontoblockthetrafficandlogthematch,ortosimplylogit.Youcanalsosettheaction
toDisabledtoremovetherulechainfromactivestatusandstopcomparingtrafficagainstthoserules.
TheCustomRulesfeature
canbeenabledordisabledusingtheEnableCustomRulesglobalsetting.
ConfiguringApplicationProfiling
YoucancreateURLprofilesbyputtingtheSonicWallSMA/SRAapplianceintolearningmodewhileapplications
areinusebytrustedusers,andthenusethoseURLprofilestogeneraterulechainsthatpreventmalicious
misuseoftheapplications.
Toconfigureapplicationprofilingandautomaticallygeneraterules:
1NavigatetotheWebApplicationFirewall>Rulespage.
NOTE:Rulechainsareenforcedintheorderthattherulechainswereadded.Thisordercanbechanged
bydeletingandre‐creatingrulechains.
Similarly,ruleswithinrulechainsareenforcedintheorderthattheruleswereadded.Thisordercanbe
changedbydeletingandre‐creating
rules.
NOTE:ApplicationprofilingissupportedontheSMA400,SRA4600,andSMA500vVirtualApplianceonly.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
41
2UnderApplicationProfiling,selectoneormoreportalswiththeapplication(s)tobeprofiledfromthe
Portalsdrop‐downlist.UseShift+clickorCTRL+clicktoselectmultipleportals.
3ForContentTypes,selectthetypeofcontenttobeprofiled:
•All–Includesallcontenttypessuchasimages,HTML,andCSS.
•HTML/XML
–Selectedbydefault,thisisthemostimportantfromasecuritystandpoint,because
ittypicallycoversthemoresensitivewebtransactions.
•Javascript–AppropriateforanapplicationwritteninJavascript.
•CSS–SelectCSStoprofilethecascadingstylesheetcontentusedtocontroltheformattingofweb
pageswritten
inHTML,XHTML,orXMLvariants.
4 ClickBeginProfilingtostartthe“learning”process.Trustedusersshouldbeusingtherelevant
applicationsontheselectedportalduringtheactiveprofilingperiod.TheBeginProfilingbuttonchanges
toEndProfiling.ProfilingcontinuesuntilyouclickEndProfiling.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
42
Duringprofiling,theSonicWallSMArecordsinputsandstoresthemasURLprofiles.TheURLprofilesare
listedasatreestructureontheWebApplicationFirewall>RulespageintheApplicationProfiling
section.
5Afteraperiodoftimeadequatetorecordinputsfromnormalapplicationuse,clickEndProfiling
tostop
theprofilingprocess.
6 OptionallyclickanyofthelinksintheURLprofiletreedisplaytoeditthelearnedvalues.Theeditingpage
fortheclickedURLisdisplayed.ClickExpandtoexpandallURLsatthatlevelinthetree.
7Toaddavalue,typethevalueinto
thefieldnexttotheparameterandthenclicktheplusbutton.To
removeavalue,selectitinthelistandthenclicktheminusbutton.
8 ClickAcceptwhenfinishedediting.RepeatforotherURLsasneeded.
9BeforegeneratingtherulesfromtheURLprofiles,selectoneofthefollowingactions
fromtheDefault
ActionforgeneratedRuleChainsdrop‐downlist:
• Disabled–Thegeneratedruleswillbedisabledratherthanactive.
•DetectOnly–Contenttriggeringthegeneratedrulewillbedetectedandlogged.
•Prevent–Contenttriggeringthegeneratedrulewillbeblockedandlogged.
10 SelectOverwriteexistingRuleChains
forURLProfilestooverwriterulechainsthathavealreadybeen
generatedfromaURLprofile.
11 ClicktheGenerateRulesbuttontogeneraterulesfromtheURLprofiles.IfaURLprofilehasbeen
modified,thosechangesareincorporated.
Ifrulechainsaresuccessfullygenerated,thestatusbarindicateshowmany
rulechainsweregenerated,
includinganythatwereoverwritten.
12 Ifyoudonotwanttoacceptthegeneratedrulechains,clicktheDeleteSelectedRuleChainsbutton,
whichisavailablebelowtherulechainlist.Alloftheautomaticallyaddedrulechainsarepre‐selected
rightaftergenerationforeasydeletion
ofthegroup.
13 ClickAccepttoapplythegeneratedrulechainstotheSonicWallSMAconfiguration.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
43
ConfiguringRuleChains
Youcanadd,edit,deleteandclonerulechains.Examplerulechains(withRuleChainIDgreaterthan15000)are
availableinthemanagementinterfaceforadministratorstouseasreference.Thesecannotbeeditedor
deleted.YoucanviewtherulesassociatedwiththerulechainbyclickingitsEdit
RuleChainiconunder
Configure.
Foreaseofconfiguration,youcancloneexamplerulechainsorregularrulechains.Cloningarulechainclones
allrulesassociatedwiththechain.Aftercloningtherulechain,youcanedititbyclickingitsEditRuleChainicon
underConfigure.
AddingorEditingaRuleChain
Toaddoreditarulechain:
1OntheWebApplicationFirewall>Rulespage,clicktheAddRuleChainbuttontoaddanewrulechain.
Toeditanexistingrulechain,clickitsEditRuleChainiconunderConfigure.
TheNewRuleChainscreenorthescreenfortheexistingrulechaindisplays.Bothscreenshave
thesame
configurablefieldsintheRuleChainsection.
2OntheNewRuleChainpage,typeadescriptivenamefortherulechai nintheNamefield.
3 SelectathreatlevelfromtheSeveritydrop‐downlist.YoucanselectHIGH,MEDIUM,orLOW.
4 SelectPrevent,DetectOnly ,or
DisabledfromtheActiondrop‐downlist.
•Prevent–Blocktrafficthatmatchestherule.
•Detect–Allowthetraffic,butlogit.
• Disabled–Therulechainshouldnottakeeffect.
TheDisabledoptionallowsyoutotemporarilydeactivatearulechainwithoutdeletingitsconfiguration.
5IntheDescriptionfield,type
ashortdescriptionofwhattherulechainwillmatchorotherinformation.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
44
6 SelectacategoryforthisthreattypefromtheCategorydrop‐downlist.Thisfieldisforinformational
purposes,anddoesnotchangethewaytherulechainisapplied.
7UnderCounterSettings,toenabletrackingtherateatwhichtherulechainisbeingmatchedandto
configureratelimiting,
selectEnableHitCounters.Additional fieldsaredisplayed.
8IntheMaxAllowedHitsfield,enterthenumberofmatchesforthisrulechainthatmustoccurbefore
theselectedactionistriggered.
9IntheResetHitCounterPeriodfield,enterthenumberofsecondsallowedtoreachtheMaxAllowed
Hits
number.IfMaxAllowedHitsisnotreachedwithinthistimeperiod,theselectedactionisnot
triggeredandthehitscounterisresettozero.
10 SelectTrackPerRemoteAddresstoenforceratelimitingagainstrulechainmatchescomingfromthe
sameIPaddress.Trackingperremoteaddressusesthe
remoteaddressasseenbytheSonicWall
SMA/SRAappliance.ThiscoversthecasewheredifferentclientssitbehindafirewallwithNATenabled,
causingthem toeffectivelysendpack etswiththesamesourceIP.
11 SelectTrackPerSessiontoenableratelimitingbasedonanattacker’sbrowsersession.Thismethodsets
acookieforeachbrowsersession.TrackingbyusersessionisnotaseffectiveastrackingbyremoteIPif
theattack erinitiatesanewusersessionforeachattack.
12 ClickAccepttosavetherulechain.ARuleChainIDisautomaticallygenerated.
13 Next,addoneormorerulesto
therulechain.SeeConfiguringRulesinaRuleChainonpage45for
detailedinformation.
CloningaRuleChain
Toclonearulechain:
1OntheWebApplicationFirewall>Rulespage,clickitsCloneRuleChainiconunderConfigure.
2 ClickOKintheconfirmationdialogbox.
Youcannowedittherulechaintocu stomizeit.SeeAddingorEditingaRuleChainonpage43.
DeletingaRuleChain
Todeletearulechain:
1OntheWebApplicationFirewall>Rulespage,clicktheDeleteRuleChainiconunderConfigurefor
therulechainyouwanttodelete.
2 ClickOKintheconfirmationdialogbox.
3 ClickAccept.
CorrectingMisconfiguredRuleChains
Misconfiguredrulechainsarenotautomaticallydetecte datthetimeofconfiguration.Whenamisconfiguration
occurs,theadministratormustloginandfixordeletethebadrules.
NOTE:Deletingarulechainalsodeletesalltheassociatedrules.
NOTE:Ifanyrulesorrulechainsaremisconfigured,theappliancewillnotenforceanycustomrulesorrule
chains.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
45
Itisdifficulttodetectafalsepositivefromamisconfiguredrulechainunlessauserrunsintoitandreportsitto
theadministrator.IftherulechainhasbeensettoPREVENT,thentheuserwillseetheWebApplicationFirewall
blockpage(asconfiguredontheWebApplication
Firewall>Settingspage).Ifnot,therewillbealogmessage
indicatingthatthe“threat ”hasbeendetected.
Considerascenarioinwhichtheadministratorinadvertentlycreatesacustomrulechainthatblocksaccesstoall
portalsoftheSonicWallSMA/SRAappliance.Forexample,theadminmayhavewanted
toenforcearuleforan
ApplicationOffloadingportal.However,heorsheforgottoaddanotherruletonarrowthecriteriaforthematch
torequestsforthatportal,hostorURL.Ifthefirstrulewastoobroad,thenthiswillmeanadenialofservicefor
theappliance.
Specifically,theadministratorcreatesarulechaintodenyusingtheGETHTTPmethodfora
specificURL,whichexpectsaPOSTrequest.
Forthis,theadministratorneedstocreatetworules:
1ThefirstruleistomatchGETrequests.
2ThesecondruleistomatchaspecificURL.
Iftheadministratorforgetstocreatethesecondrule,thenaccesstotheSonicWallSMA/SRAappliancewillbe
denied,becausethewebmanagementinterfacedependsontheGETmethod.
Tofixamisconfiguredrulechain:
1Pointyourbrowsertohttps://<SonicWallSMAIP>/cgi‐bin/welcome.
IfyoutrytoreachthewelcomepagebysimplyusingtheURLhttps://<SonicWallSMAIP>/,theusual
redirecttohttps://<SonicWallSMAIP>/cgi‐bin/welcomemaynotwork.Torepairmisconfiguredrules,
youneedtoexplicitlygotohttps://<SonicWallSMAIP>/cgi‐bin/welcome,
where<SonicWallSMAIP>is
thehostnameorIPaddressofyourSonicWallSMA/SRAappliance.
2Loginasadmin.
3NavigatetotheWebApplicationFirewall>Rulespage.
4Editordeletethebadrules.
5 ClickAccept.
ConfiguringRulesinaRuleChain
Youcanadd,edit,deleteandclonerules.Aruleisaconditionthatischeckedagainstinboundoroutbound
HTTP(S)traffic.Eachrulechaincanhaveoneormorerulesconfigured,andmusthaveatleastonerulebeforeit
canbeused.AddRulePageshowstheAddRule
page.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
46
AddRulePage
Rulesallowtheadministratortoemploybothapositivesecuritymodelandanegativesecuritymodel.Ina
positivesecuritymodel,policiesarewrittenonlytoallowknowntrafficandblockeverythingelse.
Arulehasseveralcomponents:
•Variables–TheseareHTTPprotocolentitiesthatarescannedby
WebApplicationFirewalltohelp
identifylegitimateorillegitimatetraffic.Multiplevariablescanbematchedagainsttheconfiguredvalue
intheValuefield.The ‘+’and‘‐’buttonsallowyoutoaddvariablesfromtheVariablesdrop‐downlistor
deletethemfromthelistofselectedvariables.You
cancombinemultiplevariablesasrequiredtomatch
thespecifiedvalue.Ifmultiplevariablesareconfigured,thentheruleismatchedifanyoneofthe
configuredvariablesmatchesthetargetvalue.SeeAboutVariablesonpage47formoreinformation
aboutvariables.
•Operators–Thesearearithmeticandlogicaloperators.
Notisaninversionoperatorusedtomatchany
valueexcepttheconfiguredcondition.SeeAboutOperatorsonpage49formoreinformationaboutthe
operators.
•Value–Thisentitycanbeanumber,literalstring,oraregularexpression.Itiscomparedwiththevalue
oftheconfiguredvariable(s)according
tothespecifiedoperator.Tocomparethevariable(s)tomorethan
onevalue,youcanentermultiplevaluesseparatedbyspacesintotheValuefield,andselectthe
MatchesKey w ordoperator.DelimitingbyspacesonlyworksiftheMatchesKeywordoperatoris
selected.
•Anti‐EvasiveMeasures–Thisfieldallowsyou
toapplyoperationsbeyondthosesupportedbythe
Operatorsfield,especiallytoenforceAnti‐Evasiveprotection.SeeAboutAnti‐EvasiveMeasuresonpage
50formoreinformationabouttheseoperations.
Thefollowingsectionsprovidedetailedinformationaboutrules:
• AbouttheTips/HelpSidebaronpage47
• AboutVariablesonpage47
• About
Operatorsonpage49

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
47
• AboutAnti‐EvasiveMeasuresonpage50
• ExampleUseCasesforRulesonpage51
• DeletingaRuleonpage54
• CloningaRuleonpage54
• AddingorEditingaRuleonpage54
AbouttheTips/HelpSidebar
YoucanselectavariableintheVariablesdrop‐downlisttodisplaymoreinformationaboutthatvariableinthe
Tips/Helpsidebar.ThesidebarexplainswheneachvariablewouldbeusedandwhereitisfoundintheHTTP
protocol.Anexampleusecaseisprovidedforeachvariable.
Youcan
alsoselectanentryintheAnti‐EvasiveMeasuresdrop‐downlisttodisplaymoreinformationaboutit
intheTips/Helpsidebar.
Thesidebaralsoprovidescontext‐sensitivesearch.Whenyouclickonavariableandthensearchforaparticular
keyword,thesearchresultsareonlyrelatedtovariables.
AboutVariables
VariablesareHTTPprotocolentitiesthatarescannedbyWebApplicationFirewalltohelpidentifylegitimateor
illegitimatetraffic.MultiplevariablescanbematchedagainsttheconfiguredvalueintheValuefield.The‘+’and
‘‐’buttonsallowyoutoaddvariablesfromtheVariablesdrop‐downlistordelete
themfromthelistofselected
variables.
Youcancombinemultiplevariablesasrequiredtomatchthespecifiedvalue.Ifmultiplevariablesare
configured,thentheruleismatchedifanyoneoftheconfiguredvariablesmatchesthetargetvalue.
Avariablecanrepresentasinglevalueoracollection.
Ifavariablerepresentsacollection,suchasParam eter
Values,thenaspecificvariablewithinthecollectioncanbeconfiguredbyenteringitsnameintheselectiontext
boxtotherightofthecolon(:).Forexample,thevaluefortheURIorHostvariableisuniquein
eachHTTP(S)
request.Forsuchvariables,theselectiontextboxisnotdisplayed.Othervariables,suchasRequestHeader
ValuesandResponseHeaderNames,representacollection.
Ifyouneedtotestthecollectionitselfagainstaninput,thenyouwouldleavetheselectiontextboxempty.
However,ifyou
needtoretrievethevalueofaspecificiteminthecollection,youwouldspecifythatiteminthe
selectiontextbox.Forexample,ifyouneedtotestiftheparameterpasswo rd existsinthe HTTP(S)request,
thenyouwouldconfigurethevariableParameterNamesandleavetheselectiontext
boxempty.Youwouldset
theOperatortoStringequalsandtheValuetopa s swo rd.But,ifyouwanttocheckwhetherthevalueofthe
passwordparametermatchesaparticularstring,suchas“foo”,thenyouwouldselectthePa ra mete rValues
variableandspecifypasswordintheselectiontext
box.IntheValuefield,youwouldenterfoo.
TheVariablesforuseinrulestabledescribestheavailablevariables.
Variablesforuseinrules
VariableName Collection Description
Host No ReferstothehostnameortheIPaddressintheHostheaderofanHTTP
request.Thistypicallyreferstothehostpartof
theURLintheaddressbarof
yourbrowser.
URI No ReferstothecombinationofpathandthequeryargumentsinaURL.
HTTPMethod No Referstothemethod,suchasGETandPOST,usedbythebrowsertorequest
aresourceonthewebserver.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
48
HTTPStatusCode No Referstotheresponsestatusfromthewebserver.Youcanusethisto
configureactionsforvariouserrorcodesfromthewebserver.
ParameterValues Yes Referstothecollectionofallrequestparametervalues,includingthevalues
ofallqueryargumentsandformparametersthatarepartofthe
current
request.
Tomatchagainstsomeaspectoftheentirelistofparametervalues,suchas
thenumberofparametervalues,leavetheselectionfieldempty.
Tomatchagainstthevalueofaparticularparameter,specifythenameof
theparameterintheselectionfieldtotherightofthecolon.
Parameter
Names Yes Referstothecollectionofallrequestparameternames,includingthenames
ofallqueryargumentsandformparametersthatarepartofthecurrent
request.
Tomatchagainstsomeaspectoftheentirelistofparameternames,leave
theselectionfieldempty.
Tomatchagainstthenameofaparticularparameter,
specifytheparameter
nameintheselectionfieldtotherightofthecolon.
RemoteAddress No Referstotheclient'sIPaddress.Thisvariableallowsyoutoalloworblock
accessfromcertainIPaddresses.
RequestHeader
Values
Yes ReferstothecollectionofallHTTP(S)requestheadervaluesforthecurrent
request.
To
matchagainstsomeaspectoftheentirelistofrequestheadervalues,
leavetheselectionfieldempty.
Tomatchagainstaparticularheadervalue,specifythenameoftheheader
intheselectionfieldtotherightofthecolon.
Forexample,toblockAjaxrequests,selectRequestHeaderValuesas
the
Variable,specifyX‐Request‐Withintheselectiontextbox,andspecifyajax
intheValuefield.
RequestHeader
Names
Yes ReferstothecollectionofallHTTP(S)requestheadernamesforthecurrent
request.
Tomatchagainstsomeaspectoftheentirelistofrequestheadernames,
leavetheselectionfield
empty.
Tomatchagainstaparticularheadername,specifythenameoftheheader
intheselectionfieldtotherightofthecolon.
Forexample,toblockrequeststhatarenotreferredbyatrustedhost,select
Req uestHeaderNamesastheVariable,specifyReferrerintheselection
textbox,
enterthehostnamesorIPaddressesofthetrustedhostsinthe
Valuefield,selectNotandselecttheMatchesKeywordoperator.
ResponseHeader
Values
Yes ReferstothecollectionofallHTTP(S)responseheadervaluesforthecurrent
request.
Tomatchagainstsomeaspectoftheentirelistofresponse
headervalues,
leavetheselectionfieldempty.
Tomatchagainstaparticularheadervalue,specifythenameoftheheader
intheselectionfieldtotherightofthecolon.
Variablesforuseinrules(Continued)
VariableName Collection Description

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
49
AboutOperators
Thereareanumberofarithmeticandlogicaloperators.Notisaninversionoperator,whichresultsinamatch
foranyvalueexcepttheconfiguredcondition.
TheseoperatorscanbeusedinconjunctionwithAnti‐EvasiveMeasures.Forexample,youmightusethe
Equ alsStringoperatorwithConverttoLowercaseor
NormalizeURIPa thinAnti‐EvasiveMeasures.
TheRuleoperatorstabledescribestheavailableoperatorsforusewithrules.
ResponseHeader
Names
Yes ReferstothecollectionofallHTTP(S)responseheadernamesforthecurrent
request.
Tomatchagainstsomeaspectoftheentirelistofresponseheadernames,
leavethe
selectionfieldempty.
Tomatchagainstaparticularheadername,specifythenameoftheheader
intheselectionfieldtotherightofthecolon.
Response
ContentLength
No Referstothesizeoftheresponsepayload.
ResponsePayload No Referstothewebpagecontentthatisdisplayedtotheuser.
PortalHostname No Refersto
thevirtualhostnameoftheSonicWallSMAportalwhichaccepts
therequestfromtheclient.
Tocreatearulechainthatappliestoaparticularvirtualhost,onerulewould
matchthehostandanotherwouldspecifyothercriteriaforthematch.
PortalAddress No ReferstotheIPaddressorvirtual
IPaddressoftheSonicWallSMAportal
whichacceptstherequestfromtheclient.
RequestPath No Referstotherelativepathusedtoaccessaparticularresourceinawebsite.
Ruleoperators
Operator Type Description
Contains String Oneormoreofthescannedvariablescontainsthecontent
oftheValuefield.
EqualsString String Thescannedvariable(s)matchthe
alphanumericstringin
theValuefieldexactly.
= Arithmetic ThescannedvariableisequaltothecontentoftheValue
field.
> Arithmetic Thescannedvariableisgreaterthanthecontentofthe
Valuefield.
>= Arithmetic Thescannedvariableisgr eaterthanorequaltothecontent
oftheValuefield.
< Arithmetic Thescannedvariableislessthan
thecontentoftheValue
field.
<= Arithmetic Thescannedvariableislessthanorequaltothecontentof
theValuefield.
Variablesforuseinrules(Continued)
VariableName Collection Description

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
50
AboutAnti‐EvasiveMeasures
Anti‐evasivemeasuresareappliedtoinputidentifiedbytheselectedvariablesbef oretheinputismatched
againstthespecifiedvalue.Forinstance,theStringLengthoperationisusedtocomputethelengthofthe
matchedinputanduseitforcomparison.Someoftheanti‐evasivemeasuresareusedto
thwartattemptsby
hackerstoencodeinputstobypassWebAppli cationFirewallrules.Youcanclickonananti‐evasivemeasurein
thelisttoreadmoreinformationonitintheTips/Helpsidebar.
Theanti‐evasivemeasurescanbeusedinconjunctionwithregularoperators.Therearetenoperationsto
choosefromintheAnti‐EvasiveMeasuresfield,includingtheNoneoperationwhichleavestheinputalone.
Multipleanti‐evasivemeasurescanbeselectedtogetherandindividuallyenforced.Youcanselectmultiple
measuresbyholdingtheCtrlkeywhileclickinganadditionalmeasure.WhentheNonemeasureisselected
alongwith
othermeasuresinyourrule,theinputiscomparedasisandalsocomparedafterdecodingitor
convertingitwithanothermeasure.
TheAnti‐EvasiveMeasuresforRulestabledescribestheanti‐evasivemeasuresavailableforusewithrules.
MatchesKeyword String Oneormoreofthescannedvariablesmatchesoneof
the
keywordsintheValuefield. Ifmultiplekeywordsare
specified,theyshouldbeseparatedbyspaces.
MatchesRegex String Oneormoreofthescannedvariablesmatchestheinthe
Valuefield.Anexampleofaregularexpressionthat
matchesanyfourdecimalnumbersis\d{4}.
Anti‐EvasiveMeasuresforRules
Operation Description
None Use
theNonemeasurewhenyouwanttocomparethescannedinputtothe
configuredvariable(s)andvalue(s)withoutchangingtheinput.
StringLength UsetheStringLengthoperationwhentheselectedvariableisastringandyouwant
tocomputethelengthofthestringbeforeapplyingtheselectedoperator.
Convertto
Lowercase UsetheConverttoLowercasemeasurewhenyouwanttomakecase‐insensitive
comparisonsbyconvertingtheinputtoalllowercasebeforethecomparison.When
youusethismeasure,makesurethatstringsenteredintheValuefieldareallin
lowercase.
Thisisananti‐evasivemeasuretopreventhackers
fromchangingcasetobypassthe
rule.
NormaliseURIPath UsetheNormaliseURIPathmeasuretoremoveinvalidreferences,suchas
back‐references(exceptatthebeginningoftheURI),consecutiveslashes,and
self‐referencesintheURI.Forexample,theURIwww.eshop.com/././//login.aspxis
convertedtowww.eshop.com/login.aspx.
Thisisan
anti‐evasivemeasuretopreventhackersfromaddinginvalidref erencesin
theURItobypasstherule.
RemoveSpaces UsetheRem ov e Spacesmeasuretoremovespaceswithinstringsintheinputbefore
thecomparison.Extraspacescancausearuletonotmatchtheinput,butare
interpretedbythe
backendwebapplication.
Thisisananti‐evasivemeasuretopreventhackersfromaddingspaceswithinstrings
tobypasstherule.
Ruleoperators(Continued)
Operator Type Description

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
51
ExampleUseCasesforRules
Thissectionprovidesexamplesofpositiveandnegativesecuritymodels,aswellasseveralexamplesshowing
theuseofanti‐evasivemeasurestoprovideadeeperunderstandingoftheseanti‐evasivetechniques.
Example–PositiveSecurityModel:BlockingBadLogins
TopreventlogintoanApplicationOffloadedwebsiteifthelengthofthepasswordislessthan8characters,you
wouldcreatearulechaincontainingthefollowingtworules:
1 SelectHostastheVariableandclick+toaddit,settheOperatortoEqualsString,andsetValue
tothe
VirtualHostnameoftheportal.ThischecksthattheHostheaderoftheloginrequestmatchesthesite
youaretryingtoprotect.Inthiscase,therulechainisonlybeingappliedtoonesite.
2 SelectParameterValueastheVariableandtypepasswordintotheselection
field,thenclick+toaddthe
variableandselecteditemtotherule,settheOperatorto< (lessthan),andsetValueto8.SelectString
LengthintheAnti‐EvasiveMeasureslisttocomputethelengthofthepasswordformparameter.
Base64Decode UsetheBase64Decodemeasure
todecodebase64encodeddatabeforethe
comparisonismadeaccordingtotherule.
SomeapplicationsencodebinarydatainamannerconvenientforinclusioninURLs
andinformfields.Base64encodingisdonetothistypeofdatatokeepthedata
compact.Thebackendapplicationdecodesthedata.
Thisisananti‐evasivemeasuretopreventhackersfromusingbase64encodingof
theirinputtobypasstherule.
HexadecimalDecode UsetheHexadecimalDecodemeasuretodecodehexadecimalencodeddatabefore
thecomparisonismadeaccordingtotherule.
Thisisananti‐evasivemeasuretopreventhackersfromusinghexadecimal
encoding
oftheirinputtobypasstherule.
URLDecode
URLDecode(Unicode)
UsetheURLDecodemeasuretodecodeURLencodedstringsintheinput.Usethe
URLDecode(Unicode)measuretohandle%uXXXXencoding.URLencodingisused
tosafelytransmitdataovertheinternetwhenURLscontaincharactersoutside
the
ASCIIcharacterset.
NOTE:Donotusethesemeasuresagainstaninputthathasbeendecodedalready.
Thisisananti‐evasivemeasuretopreventhackersfromusingURLencodingtobypass
rules,knowingthatthebackendwebservercaninterprettheirmaliciousinputafter
decodingit.
Forexample,theURI
www.eshop.com/hack+URL%3Bisconvertedto
www.eshop.com/hackURLbythisoperatorbeforethecomparisonismade.
Trim UsetheTrimmeasuretoremovespacesbeforeandaftertheinputdatabeforethe
comparison.Extraspacescancausearuletonotmatchtheinput,butareinterpreted
bythebackendwebapplication.
Thisis
ananti‐eva sivemeasuretopreventhackersfromaddingspacesbeforeand
aftertheinputdatatobypasstherule.
Anti‐EvasiveMeasuresforRules(Continued)
Operation Description

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
52
TheactionfortherulechainwouldbesettoPrevent.ExampleRuleChain–BlockingBadLoginsshowstherule
chainforthisexample.
ExampleRuleChain–BlockingBadLogins
Example–PositiveSecurityModel:BlockingaFormSubmissionwith
UnwantedParameters
Thisrulechainblocksaformsubmissioniftheformhasarequestparameterotherthanfor mId orifthevalueof
formIdcontainsmorethanfourdigits.Toaccomplishthis,youwouldneedtworulechains:
1Thefirstrulechaincontainstworules:
• ThefirstruleidentifiestheURLwhere
theformissubmitted.
• ThesecondrulechecksifParameterNamesdoesnotmatchthenameofthevalidparameter,
formId. ItusestheEqualsStringoperatorwiththeNotinversioncheckboxselected.
2Thesecondrulechaincontainstworules:
• ThefirstruleidentifiestheURLwheretheformis
submitted.
• ThesecondrulechecksifthevaluecontainedbytheParameterValue:formIdvariablematches
the^\d{1,4}$whichmatchesanythingthatdoesnotconsistof1to4digits.TheNotinversion

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
53
checkboxisselectedtochangetheruletomatchanythingthatdoesnotconsistofonetofour
digits.
Example–NegativeSecurityModel:BlockingMaliciousInputtoaForm
Toblockmaliciousinputtoaform,youwouldcreatearulechaincontainingthefollowingtworules:
1ThefirstruleidentifiestheURLfortheform.
2Thesecondruleidentifiestheformparameter,shell_cmdandthebadinput,traceroute.
Example–UsingURLDecodeandNone
IfahackerperceivesthataRequestURIisbeingscannedforCRandLFcharacters(carriagereturnandlinefeed),
thehackermayattempttosneakthosecharactersintotherequestbyperformingURLencodingonthe
charactersbeforeaddingthemtotherequest.TheURIwillthencontain%0D
and%0Acharacters,whichcould
beusedtolaunchanHTTPresponsesplittingattack.TheURLDecodeand/orURLDecode(Unicode)
operationscanbeusedtothwartthistypeofattackbydecodingthescannedinputbeforecomparingitagainst
theconfiguredvalue(s)tocheckforamatch.
Specifically,ifa
requestismadetotheURIhttp://www.host.com/foo%20bar/andtheURLDecodeoperationis
selected,thescannedURIbecomeshttp://www.host.com/foobar/afterdecoding,whichcannowbesafely
matched.Tothwartahackerwhosendsanon‐encodedrequestinadditiontotheencodedone,the
administratorcanselecttheNone
andtheURLDecodeoptionsintherule.
Example–UsingConverttoLowercaseandURLDecodewithParameterValues
AnadministratorwantstocheckwhetherthecontentofthevariableParameterValuesmatchesthevaluefo o
barinordertoblocksucharequest.Becausethebackendapplicationacceptscase‐insensitiveinputs(foobar
andFOOBAR),thehackercanpassfooBAR intherequestandevadetherule.
Topreventthisevasion,the
administratorspecifiesConverttoLowercaseasananti‐evasiveoperationandconfiguresthevalueasfoo bar
inalllowercase.Thiscausesallrequestparametervaluestobeconvertedtolowercaseandcomparedagainst
thevalueforacase‐insensitivecheck.
Similarly,the
hackercouldpassfoo%20BAR,whichistheURLencodedversiontypicallyusedbybrowsers.To
preventthisevasion,theadministratorspecifiesURLDecodeastheanti‐evasiveoperationtoapplytothe
requestentity.Theinputfoo%20BARisURLdecodedtofo oBAR .IftheinputisalreadyfooBAR
,thenURL
decodingisnotapplied.
Example–UsingStringLengthandURLDecodewithParameterValues:ID
ComparingagainstadecodedinputallowstheadministratortousetheStringLengthmeasuretocheckthe
lengthoftheinputagainstthematchingvariable.Forexample,ifawebapplicationIDparametershouldnotbe
morethanfourcharacters,theadministratorcouldselectParam eterValuesintheVariablefield,enter
IDin

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
54
theselectionfield,click+toaddthevariableandselecteditemtotherule,enter4intheValuefield,select>in
theOperatorlist,andselectbothURLDecodeandStringLengthintheAnti‐EvasiveMeasureslist.
DeletingaRule
Todeletearulefromarulechain:
1OntheWebApplicationFirewall>Rulespage,clicktheEditRuleChainiconunderConfigureforthe
rulechainfromwhichyouwanttodeletearule.Thepageforthatrulechainopens.
2 ClicktheDeleteiconunderConfigurefortheruleyouwanttodelete.
3 ClickOKinthe
confirmationdialogbox.
4 ClickAccept.
CloningaRule
Toclonearule:
1OntheWebApplicationFirewall>Rulespage,clicktheEditRuleChainiconunderConfigureforthe
rulechainwhichcontainstheruleyouwanttoclone.Thepageforthatrulechainopens.
2 ClicktheCloneiconunderConfigurefortheruleyouwanttoclone.
3 ClickOKinthe
confirmationdialogbox.
Youcannowedittheruletocustomizeit.SeeAddingorEdi ting aRul eChainonpage43.
AddingorEditingaRule
Toaddoreditaruleinarulechain:
1 ClicktheEditRuleChainiconunderConfigurefortherulechainonwhichyouwanttoaddoredita
rule.Thepageforthatrulechainopens.
2 ClicktheAddRulebuttontoaddanewrule,orclickthe EditiconunderConfigurefortheruleyouwant
toedit.
3IntheAddRulepageorthepagefortheeditedrule,selectavariablefromtheVariablesdrop‐downlist.
SeeAboutVariablesonpage47forinformationabouttheavailablevariables.
4Ifthechosenvariableisacollectionofvariables,aselectionfieldisdisplayedtotheright
oftheVariables
field,afterthecolon.Ifyouwishtomakeacomparisonagainstaparticularmemberofthecollection,
typethenameofthatitemintotheselectionfield.
Totestthecollectionitselfagainstaninput,leavetheselectionfieldblank.Forexample,totestwhether
acertain
parameterexistsintherequest,youcouldselecttheParameterNamesvariableandthentype
thespecificparameternameintotheValuefield(butnotintothevariableselectionfield).
5 ClickthePlusbuttontoaddthevariabletotherule.RepeatStep2throughStep5toaddmore
variables.
Todeleteavariable,selectitinthelargetextboxandclicktheMinusbutton .

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
55
6 Selectastringorarithmeticoperat orfromtheOperatorsdrop‐downlist.Toperformtheinverse
operation,selectNot.
7IntheValuefield,typeinthe valuetobecomparedwiththeselectedvariable(s)inthescannedHTTP(S)
input.Tocomparetheinputagainstmultiplevalues,typeineachvalueseparated
byaspace.Eachvalue
willbecomparedindividually.
8 SelectoneormoremeasuresfromtheAnti‐EvasiveMeasureslist.HoldtheCtrlkeyonyourkeyboard
whileclickingtoselectmultiplemeasures.
9 ClickAcceptwhenfinished.
UsingWebApplicationFirewallMonitoring
TheWebApplicationFirewall>Monitoringpageprovidestwoscreens:LocalandGlobal.Bothscreensdisplay
statisticsandgraphsfordetected/preventedthreatsovertimeandtop10threats.TheLocalscreenalsodisplays
webserverstatusstatisticsandgraphsofthenumberofrequestsandtheamountoftrafficduring
theselected
monitoringperiod.
Themonitoringfunctionsofeachscreenar eexplainedinthefollowingsections:
• MonitoringontheLocalScreenonpage55
• MonitoringontheGlobalScreenonpage60
MonitoringontheLocalScreen
TheLocalscreendisplaysstatisticsandgraphsforthelocalappliance.GraphsaredisplayedforWebSer ver
StatusandWAFThreatsDetected&Prevented.Forthelatter,youcanusethePerspectiveoptionstochangethe
viewbetweenSignature,Severity,andSer ver,andyoucandisplaythestatisticsinlistformat
ratherthanas
graphs.
UsingtheControlButtons
Thecontrolbuttonsaredisplayedatthetopofthescreen.Theycontrolthestatisticsthataredisplayedonthis
screen.OntheLocalscreen,youcanusethecontrolbuttonstoturnstreamingupdatesonoroff,refreshthe
dataonthescreen,clearthegraphs,anddownloadareport.
Ifstreamingisturnedon,WebApplicationFirewall
statisticsinformationisfetchedperiodically,anddisplayedinthegraphsandthreatlist.Ifstreamingisturned
off,nonewinformationcanbedisplayed.
Tousethecontrolbuttons:
1 SelecttheLocalscreen.Theactivescreennameisdisplayedinblue,whiletheinactivescreennameis
white.Thecontrolbuttonsactonthescreenthatiscurrentlydisplayed.
2Toturnstreamingonoroff,clicktheONorOFFindicatornexttoStreamingUpdates.
3Torefreshthedisplay,click
Refresh.
4ToclearallWebApplicationFirewallstatisticsfromthegraphsandlist,clickClearGraphs.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
56
5TogenerateaPDFreportwithWebAppl icationFirewallstatistics,clickDownloadReport.
6IfpromptedtoinstallAdobeFlashPlayer,clickGetFlashandthenaftertheinstallationclickTryAgainto
generatethePDFreportfromInternetExplorer.
MonitoringWebServerStatus
OntheLocalscreen,belowthecontrolbuttons,thisscreendisplaysgraphsforwebserverstatus.Onegraph
showsthenumberofwebrequestsdetectedovertime,andanothergraphshowstheamountoftrafficin
kilobytes(KB).
Thewebserverstrackedarethoseserverswithinthelocalnetworkofthe
SonicWallSMA/SRAappliancethat
provideHTTP/HTTPS bookmarks,offloadedapplications,andotherwebservices.TheTrafficgraphindicatesthe
amountofHTTP/HTTPSpayloaddatathatissenttoclientbrowsers.
YoucanviewwebserveractivityontheLocalscreenoverdifferenttimeperiodsbyselectingoneofthe
followingoptions
fromtheMonitoringPe r i o ddrop‐downlist:
• Last60Seconds
• Last60Minutes
• Last24Hours
• Last30Days
WebServerStatusForLast24Hoursshowsa24hourperiodofwebserveractivity.
WebServerStatusForLast24Hours
NOTE:InternetExplorerrequiresAdobeFlashPlayerversion10orhighertogeneratethereport.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
57
WebServerStatusForLast60Minutesshowsa60minuteperiodofwebserveractivity.
WebServerStatusForLast60Minutes
MonitoringDetectedandPreventedThreats
OntheLocalscreenbelowthewebserverstatusgraphs,theWebApplicationFirewall>Monitoringpage
displaysgraphsindicatingthenumberofdetectedandpreventedthreats.Twographsarepresented,one
showingthenumberofthreatsovertime,andtheothershowingthetoptenthreatsthatweredetectedand
preventedduringthattimeframe.
Youcanchangethetimeframedisplayedinbothgraphsorchangetheviewtodisplayallthreat sinlistformatby
selectingoneofthefollowingoptionsfromtheMonitoringPerioddrop‐downlist:
• Last12Hours
• Last14Days
• Last21Days
• Last
6Months
• AllinLists
ThreatsOverLast21Daysshowsthenumberandseveritiesofthreatsdetectedandpreventedoverthelast21
days.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
58
ThreatsOverLast21Days
Whendisplayingthetop10threatsgraphwithPersp ectiv esettoSignature,hoveringyourmousepointerover
thesignatureIDcausesatooltiptoappearwithdetailsaboutthethreat.
ThreatDetailsTooltip
ViewingThreatsinListFormat
Toseethethreatsinlistformatratherthanasagraph,selectAllinListsfromtheMonitoringPer i od
drop‐downlist.ThreatsinListFormatshowsthelistformat.
TheSeveritycolumnofthethreatlistiscolorcodedforquickreference,asfollows:
• Highseveritythreats–Red
•
Mediumseveritythreats–Orange
• Lowseveritythreats–Black
Theinitial,defaultsortingorderliststhehighseveritythreatswithhighestfrequencyvaluesfirst.Youcan
changetheorderoflistedthreatsbyclickingonthecolumnheadingstosortthembyID,signaturename,
classification,severity,orfrequency.Click
againtotogglebetweenascendinganddescendingorder.Theactive
sortingcolumnismarkedbyanarrowheadpointingupwardsforascendingorder,anddownwardsfor
descendingorder.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
59
ThreatsinListFormat
Toviewandhidethreatdetails:
1OntheWebApplicationFirewall>Monitoringpage,selectAllinListsfromtheMonitoringPeriod
drop‐downlist.ThelistofdetectedorpreventedthreatsisdisplayedintheWAFThreatsDetected&
Preventedtable.
2Todisplaydetailsaboutathreat,clickonthethreat.Thedetailsincludethefollowing:
•URL–TheURLtotheSonicWallknowledgebaseforthisthreat
•Category–Thecategoryofthethreat
•Severity–Theseverityofthethreat,eitherhigh,medium,orlow
•Summary–Ashortdescriptionofhowthethreatbehaves
3Tocollapsethethreatdetails,clickthe threatlinkagain.
ChangingPerspective
FortheTop10Threatsgraph,youcanselectthefollowingdisplayoptionsfromthePers pec tive drop‐downlist:
• Signature–Thenameofeachthreatshownislistedattheleftsideofthegraph.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
60
• Severity–High,medium,andlowseveritythreatsaredisplayedusingcolorcoding.
• Server–Theservernamesarelistedattheleftsideofthegraph.
MonitoringontheGlobalScreen
TheGlobalscreendisplaysstatisticsandgraphsforthreatsreportedbyallSonicWallSMA/SRAapplianceswith
WebApplicationFirewallenabled.GraphsaredisplayedforWAFThreatsDetected&Prevented.
UsingtheControlButtons
Thecontrolbuttonsaredisplayedatthetopofthepage.Theycontrolthestatisticsthataredisplayedonthis
page.OntheGlobalscreen,youcanusethecontrolbuttonstoturnstreamingupdatesonoroff,refreshthe
dataonthescreen,anddownloadareport.Ifstreamingis
turnedon,WebApplicationFirewallstatistics
informationisfetchedperiodically,anddisplayedinthegraphsandthreatlist.Ifstr eamingisturnedoff,nonew
informationcanbedisplayed.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
61
Tousethecontrolbuttons:
1 SelecttheGlobalscreen.Theactivescreennameisdisplayedinblue,whi letheinactivetabnameis
white.Thecontrolbuttonsactonthescreenthatiscurrentlydisplayed.
2Toturnstreamingonoroff,clicktheONorOFFindicatornexttoStreamingUpdates.
3Torefreshthedisplay,click
theRefreshbutton.
4TogenerateaPDFreportcontainingWebApplicationFirewallstatistics,clicktheDownloadReport
button.
5IfpromptedtoinstallAdobeFlashPlayer,clickGetFlashandthenaftertheinstallationclickTryAgainto
generatethePDFreportfromInternetExplorer.
MonitoringDetectedandPreventedThreats
AtthetopoftheGlobalscreen,theWebApplicationFirewall>Monitoringpagedisplaysgraphsindicatingthe
numberofdetectedandpreventedthreats.Twographsarepresented,oneshowingthenumberofthreatsover
time,andtheothershowingthetoptenthreatsthatweredetectedandpreventedduringthat
timeframe.
Youcanchangethetimeframedisplayedinbothgraphsbyselectingoneofthefollowingoptionsfromthe
MonitoringPerioddrop‐downlist:
• Last12Hours
• Last14Days
• Last21Days
• Last6Months
ThreatsOverLast21Daysshowsthenumberandseveritiesofthreatsdetected
andpreventedoverthelast21
days.
NOTE:InternetExplorerrequiresAdobeFlashPlayerversion10orhighertogeneratethereport.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
62
ThreatsOverLast21Days
HoveringyourmousepointeroverthesignatureIDcausesatooltiptoappearwithdetailsaboutthethreat.
ThreatDetailsTooltip
Thelocalsignaturedatabaseontheapplianceisaccessedtogetdetailedthreatinformation,butifthedatabase
isnotup‐to‐date,somedetailedinformation
fortheTop10Threatsmightnotbeavailable.Inthiscase,the
threatcolorinthegraphislightgrey,andtheseverityisdisplayedasunknowninthetooltipforthisthreat.The
followingerrormessageisalsodisplayedbelowthegraphs:
“Warning:WebApplicationFirewallSignatureDatabasefor
thisdeviceisnotcurrent.Pleasesynchronizethe
DatabasefromtheWebApplicationFirewall>Statuspage”
UsingWebApplicationFirewallLogs
TheWebApplicationFirewall>Logpageprovidesanumberoffunctions,includingaflexiblesearch
mechanism,andtheabilitytoexportthelogtoafileoremailit.Thepagealsoprovidesawaytoclearthelog.
Clickingonalogentrydisplaysmoreinformationabouttheevent.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
63
Seethefollowingsections:
• SearchingtheLogonpage63
• ControllingtheLogPaginationonpage63
• ViewingLogEntryDetailsonpage64
• ExportingandEmailing LogFilesonpage64
• ClearingtheLogonpage65
SearchingtheLog
Youcansearchforavaluecontainedinacertaincolumnofthelogtable,andcanalsosearchforlogentriesthat
donotcontainthespecifiedvalue.
ToviewandsearchWebApplicationFirewalllogfiles:
1OntheWebApplicationFirewall>Logpage,typethevaluetosearchforintotheSearchfield.
2 Selectthecolumninwhichtosearchfromthedrop‐downlisttothe rightoftheSearchfield.
3Dooneofthefollowing:
• Tostartsearchingforlogentriescontainingthesearchvalue,
clickSearch.
• Tostartsearchingforlogentriesthatdonotcontainthesearchvalue,clickExclude.
• TocleartheSearchfield,setthedrop‐downlistbacktothedefault(Time),anddisplaythefirst
pageoflogentries,clickReset.
ControllingtheLogPagination
Toadjustthenumberofentriesonthelogpageanddisplayadifferentrangeofentries:
1OntheWebApplicationFirewall>Logpage,enterthenumberoflogentriesthatyouwantoneachpage
intotheItemsperPagefield.The Logpagedisplaychangestoshowthenewnumberofentries.
2Toviewthelogentriesbeginningatacertainnumber,typethestarting
numberintotheItemfieldand
pressEnteronyourkeyboard.
3Toviewthefirstpageoflogentries,clicktheleft‐mostbuttoninthearrowcontrolpad.
4Toviewthepreviouspageoflogentries,clicktheleftarrowinthearrowcontrolpad.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
64
5Toviewthenextpageoflogentries,clicktherightarrowinthearrowcontrolpad.
6Toviewthelastpageoflogentries,clicktheright‐mostbuttoninthearrowcontrolpad.
ViewingLogEntryDetails
Thelogentrydetailsvarywiththetypeoflogentry.TheURI(UniformResourceIndicator)isprovidedalongwith
thecommandfordetectedthreats.Informationabouttheagentthatcausedtheeventisalsodisplayed.Foran
explanationoftherathercrypticAgentstring,thefollowingWikipediapageprovidesa
descriptionandlinksto
externalsitesthatcananalyzeanyuseragentstring:http://en.wikipedia.org /wiki/User_agent
Toviewmoredetailsaboutanindividuallogentry:
1OntheWebApplicationFirewall>Logpage,clickanywhereonthelogentrythatyouwanttoview.The
detailsaredisplayeddirectlybeneaththeentry.
2Tocollapsethedetailsforalogentry,clickagainontheentry.
ExportingandEmailingLogFiles
YoucanexportthecurrentcontentsoftheWebApplicationFirewalllogtoafile,oremailthelogcontentsby
usingthebuttonsinthetoprightcorneroftheWebApplicationFirewall>Logpage.
Exportedfilesaresavedwitha.wrifilenameextension,andopenwithWordpad,
bydefault.
EmailedfilesareautomaticallysenttotheaddressconfiguredontheLog>SettingspageoftheSonicWall SMA
managementinterface.Ifnoaddressisconfigured,theStatuslineatthebottomofthebrowserwilldisplayan
errormessagewhenyouclicktheE‐Mai lLogbuttonon
theWebApplicationFirewall>Logpage.
Toexportoremailthelog:
1Toexportthe logcontents,clickthe ExportbuttoninthetoprightcorneroftheWebApplication
Firewall>Logpage.TheFileDownloaddialogboxisdisplayed.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
65
2IntheFileDownloaddialogbox,dooneofthefollowing:
• Toopenthefile,clickOpen.
• Tosavethefile,clickSave,thenbrowsetothefolderwhereyouwanttosavethefileandclick
Save.
3Toemailthelogcontents,clicktheE‐MailLogbutton
inthetoprightcorneroftheWebApplication
Firewall>Logpage.ThelogcontentsareemailedtotheaddressspecifiedintheLog>Settingspage.
ClearingtheLog
YoucanremoveallentriesfromtheWebApplicationFirewalllogontheWebApplicationFirewall>Logpage.
Theentriesonthepageareremoved,andanyattempttoexportoremailthelogfilewhileitisstillemptywill
causeaconfirmationdialogboxtodisplay.
TocleartheWebApplicationFirewalllog:
1OnthetoprightcorneroftheWebApplicationFirewall>Logpage,clickClear.
2 ClickOKintheconfirmationdialogbox.
ConfiguringanApplicationOffloadingPortal
BecauseWebApplicationFirewallisusedmostoftentoprotectanApplicationOffloadingportal,thissection
providesasummaryofhowtoconfiguresuchaportal.TheSonicWallSMA/SRAapplianceadministratorcan
configureweb(HTTP)orsecureweb(HTTPS)offloadedapplicationstoallowuseraccesstoweb‐basedresources
andapplications
suchasSharepoint,MicrosoftOWAPremium,orDominoWebAccess.
ApplicationOffloadingshouldsupportanyapplicationusingHTTP/HTTPS.SonicWallSMAhaslimitedsupportfor
applicationsusingwebservicesandnosupportfornon‐HTTPprotocolswrappedwithinHTTP.
Theapplicationshouldnotcontainhard‐codedself‐referencingURLs.Iftheseare
present,theApplication
OffloadingproxymustrewritetheURLs.SincewebsitedevelopmentdoesnotusuallyconformtoHTML
standards,theproxycanonlydoabest‐efforttranslationwhenrewritingtheseURLs.Specifyinghard‐coded,
self‐referencingURLsisnotrecommendedwhendevelopingawebsitebecausecontentdevelopersmust
modifythewebpageswheneverthehostingserverismovedtoadifferentIPorhostname.
Forexample,ifthebackendapplicationhasahard‐codedIPaddressandschemewithinURLsasfollows,
ApplicationOffloadingmustrewritetheURL.
<ahref="http://1.1.1.1/doAction.cgi?test=foo">
Fordetailedconfigurationinformation,seetheSonicWallSMA
ApplicationOffloadingandHTTP(S)Bookmarks
FeatureGuideortheSMA8.6AdministrationGuideat:http://www.sonicwall.com
TheApplicationOffloadingPortalSettingstableshowsappropriateApplicationOffloadingportalsettingswhen
theportalisprovidingWebApplicationFirewallprotectiontoremotelyaccessedinternalsitesandtopublic
sites.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
66
SonicWallrecommendsusingthesameFQDNfortheVirtualHostNameandtheapplicationserversitetoavoid
theneedforURLrewriting.
TooffloadaWebapplicationandcreateaportalforit:
1NavigatetoPortals>PortalsandgototheVirtualHostsection.TheVirtualHostSettingsscreenopens.
ThisallowsyoutoaccessthePortaldirectly.
2EnteradescriptivenameintheVirtualHostDomainNamefield.
3OntheOffloadingtab,selectEnableLoadBalancingforloadbalancingamongoffloadedapplication
servers.
4 SelectoneofthefollowingfromtheSchemedrop‐downlist:
•Web(HTTP)–accesstheWebapplicationusingHTTP(defaultscheme)
•SecureWeb(HTTPS)–accesstheWebapplicationusingHTTPS
•Auto(HTTP/HTTPS)–allowstheusertodeterminetheactualschemeusedtotalktothe
backendserverwhenaccessing
anoffloadingportal.Accessisstillunderthecontroloftheaccess
policy.
ApplicationOffloadingPortalSettings
ApplicationOffloadingPortal
Settings
ForRemoteAccesstoanInternal
Site
ForRemoteAccesstoaPublicSite
DNSConfiguration SplitDNS PublicDNS
Authentication Enabled Disabled(likely)
AccessPolicies User/Group/Global Global
SSLVPNDomains Enabled None
LoginCustomization Optional None
CustomLogo Optional None

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
67
WhenusingtheAutoscheme,userscantypehttp://www.example.virtual.host.com or
https://www.example.virtual.host.cominbrowser’saddressbartotestthisfeature.Evenscheme
settoAuto,it ’sstillunderthecontroloftheaccesspolicy.
• Generic(SSLOffloading)–useSSLoffloadingtoaccesscustomSSLapplications
(non‐HTTP(S)applications)
5Enterthehostname
orprivateIPaddressofthebackendhostintotheApplicationSer verHostfield.
6 OptionallyentertheIPv6addressofthebackendhostintotheApplicationServerIPv6Addressfield.
7InthePort Number(optional)field,optionallyenteracustomportnumbertouseforaccessingthe
application.
8IntheHomepage
URI(optional)field,optionallyenteraURItoaspecificresourceontheWebserverto
whichtheuserisforwardedthefirsttimetheusertriestoaccesstheApplicationOffloadingPortal.This
isastringintheformof:/exch / test . cgi?key1=value1 &key2= va l u e2
Whenthisfieldisconfigured,itredirectsthe user
totheWebsite’shomepagethefirsttimetheuser
accessestheportal.ThishappensonlywhentheuserisaccessingthesitewithnoURLpath(thatis,when
accessingtherootfolder,forexample:https://www.google.com/).Thisisnotanaliasfortherootfolder.
Theusercanedit
theURLtogobacktotherootfolder.
Thekey=valuepairsallowyoutospecifyURLqueryparametersintheURL.Youcanusetheseforany
WebsitethatdoesnothaveadefaultredirectfromtherootfoldertothehomepageURL.OutlookWeb
Accessis
oneexample,butnotethatmostpublicsitesdohaveadefaultredirect.
aUnderSecuritySettings,selectEnableWebApplicationFirewalltoenablethefeature.
b SelectDisableAuthenticationControls,AccessPolicies,andCSRFProtection(ifenabled)if
youneednoauthentication,accesspolicies,orCSRFprotectionenforced.Thisisusefulfor
publiclyhostedWebsites.
aToconfigureActiveSyncauthentication,clearDisableAuthenticationControlstodisplaythe
authenticationfields.SelectEnableActiveSyncauthenticationandthentypethedefault
domainname.Thedefaultdomainnameisnotusedwhenthedomainnameissetintheemail
client’ssetting.
9 SelectAutomaticallyLogintoconfigure
SingleSign‐Onsettings.
10 ForautomaticloginusingSSO,selectoneofthefollowingradiobuttons:
•UseSS L‐VPNaccou ntcredentials–allowlogintothe offloadedapplicationusingthe
credentialsconfiguredontheSonicWallSMA/SRAappliance.
CAUTION:ItistheAdministrator’sresponsibilitytoconfigurethecorrectschemeusedtotalktothe
backendserver. Auto(HTTP/HTTPS)SchemecanoperateonlyifHT TPaccessisenabledfortheVirtual
Host(undertheVirtualHosttab)andauthenticationisdisabled(undertheOffloadingtab)thatcanbe
insecure.Therefore,
youarepromptedtoclickOKtoenableHTTPforVirtualHost.

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
68
•Usecustomcredentials–displaysUsername,Password,andDomainfieldswhereyoucan
enterthecustomcredentialsfortheapplicationorusedynamicvariables.ForthePass wor dfield,
enterthecustompasswordtobepassed,orleavethefieldblanktopassthecurrentuser’s
passwordtotheoffloadedapplication
portal.Fortheotherfields,dynamicvariablescanbeused,
suchasthoseshowninthefollowingtable:
11 IfyouselectedAutomaticallyLogin,selectFo rm s‐basedAuthenticationtoconfigureSingleSign‐On
forforms‐basedauthentication.
• ConfiguretheUserFor m Fieldtobethesameasthe‘name’and‘id’
attributeoftheHTML
elementrepresentingUserNameintheLoginform,forexample:
<inputtype=textname=’userid’>
• ConfigurethePassw ordFo r m Fieldtobethesameasthe‘name’or‘id’attributeoftheHTML
elementrepresentingPasswordintheLoginform,forexample:
<input type=password name=’PASSWORD’ id=’PASSWORD’ maxlength=128>
12 IntheVirtualHostsection,setahostnamefortheapplicationintheVirtualHostDomainNamefield,
andoptionallyenteradescriptivealiasintheVirtualHostAliasfield.
Ifyouneedtoassociateacertificatetothishost,youshouldadditionallysetavirtualinterfaceand
importthe
relevantSSLcertificate.Youcouldavoidcreatingavirtualinterfacebyimportingawildcard
certificateforallvirtualhostsontheSonicWallSMA/SRAappliance.
SeetheSonicWallSecureMobileAccess8.6AdministrationGuideformoreinstructionsonconfiguring
thefieldsinthissection.
13 Ifauthenticationisdisabledforthisportal,you
havetheoptiontoEn ableHT TPaccessforthis
ApplicationOffloadedPortal.Thisfeatureisusefulforsettingupoffloadingintrialdeployments.
Supporteddynamicvariables
TextUsage Variable ExampleUsage
LoginName %USERNAME% US\%USERNAME%
DomainName %USERDOMAIN% %USERDOMAIN\%USERNAME%
GroupName %USERGROUP% %USERGROUP%\%USERNAME%

SonicWallSecureMobileAccess8.6FeatureGuide
ConfiguringWebApplicationFirewall
69
14 ClickAccept.YouarereturnedtothePortals>PortalspagewhereyouseetheWebapplicationlistedas
anOffloadedWebApplicationunderDescription.
15 Ifyouhavenotdisabledauthentication,navigatetothePortals>Domainspageandcreateadomainfor
thisportal.
16 UpdateyourDNSserverforthis
virtualhostdomainnameandalias(ifany).
NOTE:Inthefuture,withoutaWAFlicense,AnonymousApplicationOffloadingaccesswillnotbe
supported.ActivateaWAFsubscri ptionorusethetrialversionfromtheSystem>Licensespage.

SonicWallSecureMobileAccess8.6FeatureGuide
VerifyingandTroubleshootingWebApplicationFirewall
5
70
VerifyingandTroubleshootingWeb
ApplicationFirewall
OnewaytoverifythecorrectconfigurationofWebApplicationFirewallisbyviewingtheWebApplication
Firewall>Monitoringpage.Thispagedisplaysstatisticsandgraphsfordetected/preventedthreatsovertime
andtop10threats.TheLocalscreenalsodisplaysWebserverstatusstatisticsandgraphsofthenumberof
requestsandtheamountoftrafficduringtheselectedmonitoringperiod.Withnormaluseandexposuretothe
Internet,youshouldbegintoseestatisticswithinadayofactivation.
YoucanalsofindhelpfulinformationinboththeLog>ViewpageandWebApplicationFirewall>Logpage.This
sectionlistssomeoftherelevantlogmessagesandprovidesanexplanationorsuggestionsforactionsinthose
cases.
Log>ViewMessages
ThefollowingmessagescanbeviewedfromtheLog>Viewpage:
• LicenseManagerSSLconnectionfailed‐Restartingtheappliancecouldbenecessary
Testtheconnectivitytolicensemanager.sonicwall.comfromtheSystem>Diagnosticspageusingthe
PingandDNSLookupdiagnosticutilitiestoensurethatthereisconnectivitytothebackend
server.
• LicenseManagerFailedtoresolvehost.CheckDNS.
Testtheconnectivitytolicensemanager.sonicwall.comfromtheSystem>Diagnosticspageusingthe
PingandDNSLookupdiagnosticutilitiestoensurethatthereisconnectivitytothebackendserver.
• LicenseManagerPeerIdentityfailed‐Checkcertificatesandtime
TheLicenseManagerserveror
thesignaturedatabaseservermaynothaveavalidSSLCertificate.
• LicenseManagerResetcalled
Thedevicelicenseshavebeenreset.NavigatetotheSystem>Licensespagetoactivate,upgradeor
renewlicenses.
WebApplicationFirewall>LogandLog>ViewMessages
ThefollowingmessagescanbeviewedfromtheWebApplicationFirewall>LogpageandtheLog>Viewpage:
• WAFsignaturedatabaseupdatefailed:Nosignatureswerefoundintheupdate
Thedownloadforthedatabaseupdatecompleted,butnosuitablesignatureswerefoundinthe
database.
• WAFsignaturedatabase
updatefailed:Oldsignaturetimestampfoundintheupdate
ThetimestampfoundinthedatabaseupdatefromtheLicenseManagerisolderthanwhatwasoriginally
advertisedbeforethedownloadfortheupdatestarted.
• WAFsignaturedatabaseupdatefailed:Erroroccurredwhileprocessingtheupdate

SonicWallSecureMobileAccess8.6FeatureGuide
VerifyingandTroubleshootingWebApplicationFirewall
71
Therewasageneralerrorindownloadingandprocessingthedatabaseupdate.Thisispossibleifthedata
intheupdatedoesnotconformtothesignatureparserschema.
• WAFsignaturedatabaseupdatefailed:ErroroccurredwhiledownloadingtheWAFsignaturedatabase
update
Therewasageneralerrorindownloadingand
processingthedatabaseupdate.Thisispossibleifthedata
intheupdatedoesnotconformtothesignatureparserschema.
• WAFsignaturedatabaseupdatewasdownloadedsuccessfully. Thenewdatabasecontains<num>rules
Signaturedatabasedownloadwassuccessful.Thenewdatabasecontains<num>numberofrules.Arule
isan
internalpropertywhichwillbeusedbySonicWalltodeterminehowmanysignatureswere
downloaded.
• WAFsignaturedatabasehasbeenupdated
ThesignaturedatabaseupdatewasappliedaftertheadministratorclickedontheApplybuttononthe
WebApplicationFirewall>Statuspage.
• WAFengineisbeingstartedwiththefactory
defaultsignaturedatabase
TheWebApplicationFirewallenginewillbeusingthefactorydefaultsignaturedatabasefortraffic
inspection.Thismayimplythatnonewsignatureswerefoundsincethefirmwareupdate.Ifanattempt
todownloadisrevealedinthelogsearlier,thenthismessagecouldalsoimplythatthe
updatecouldnot
beprocessedsuccessfullyduetodatabaseerrorsandasaprecautionarymeasurethefactorydefault
databasehasbeenused.
NOTE:YoucanselecttheApplySignatureUpdatesAutomaticallyoptionontheWebApplication
Firewall>Settingspagetoapplynewsignaturesautomatically.Ifthisoptionisnotselected,youmust
clicktheApplybuttonthatappearsontheWebApplicationFirewall>Statuspageafterasuccessful
download.Afterthe
databasehasbeensuccessfullyapplied,allofthesignatureswithinthenewdatabase
canbefoundonthe WebApplicationFirewall>Signaturespage.

SonicWallSecureMobileAccess8.6FeatureGuide
SonicWallSupport
6
72
SonicWallSupport
TechnicalsupportisavailabletocustomerswhohavepurchasedSonicWallproductswithavalidmaintenance
contractandtocustomerswhohavetrialversions.
TheSupportPortalprovidesself‐helptoolsyoucanusetosolveproblemsquicklyandindependently,24hoursa
day,365daysayear.ToaccesstheSupport
Portal,gotohttps://www.sonicwall.com/support.
TheSupportPortalenablesyouto:
• Viewknowledgebasearticlesandtechnicaldocumentation
• Viewvideotutorials
• AccessMySonicWall
• LearnaboutSonicWallprofessionalservices
• ReviewSonicWallSupportservicesandwarrantyinformation
• Registerfortrainingandcertification
• Requesttechnicalsupportorcustomerservice
TocontactSonicWallSupport,visithttps://www.sonicwall.com/support/contact‐
support.

SonicWallSecureMobileAccess8.6FeatureGuide
SonicWallSupport
73
AboutThisDocument
SonicWallSMAWebApplicationFirewallFeatureGuide
Updated‐March2018
SoftwareVersion‐8.6
232‐004278‐00RevA
Copyright©2018SonicWallInc.Allrightsreserved.
SonicWallisatrademarkorregisteredtrademar kofSonic WallInc.and/oritsaffiliatesintheU.S.A.and/orothercountries.Allother
trademarksandregisteredtrademarksarepropertyoftheirrespectiveowners
TheinformationinthisdocumentisprovidedinconnectionwithSonicWallInc.and/oritsaffi liates’products.Nolicense,expressor
implied,byestoppelorotherwise,toanyintellectualpropertyrightisgrantedbythisdocumentorinconnectionwiththesaleofSonicWall
products.EXCEPTASSETFORTHINTHE TERMSANDCONDITIONSASSPECIFIEDINTHELICENSEAGREEMENTFORTHISPRODUCT,
SONICWALLAND/ORITSAFFILIATESASSUMENOLIABILITYWHATSOEVERAND
DISCLAIMSANYEXPRESS,IMPLIEDORSTATU TORY
WARRANT YRELATINGTOITSPRODUCTSINCLUDING,BUTNOTLIMITEDTO,THEIMPLIEDWARR ANT YOFMERCHANTABILITY,FITNESSFOR
APAR TI CU L A RPURPOSE,ORNON‐INFRINGEMENT.INNOEVENTSHALLSONICWALLAND/ORITSAFFILIATESBELIABLEFORANYDIRECT,
INDIRECT,CONSEQUENTIAL,PUNITIVE,SPECIALORINCIDENTALDAMAGES(INCLUDING,
WITHOUTLIM ITATION,DAMAGESFORLOSSOF
PROFITS ,BUSINESSINT ERRUP T I ON ORLOSSOFINFORMATION)ARISIN GOUTOFTHEUSEORINABILIT YTOUSETHISDOCUMENT,EVENIF
SONICWALLAND/ORITSAFFILIATESHAVEBEENADVISEDOFTHEPOSSIBILITYOFSUCHDAMAGES.SonicWalland/oritsaffiliatesmakeno
representationsorwarrantieswithrespectto
theaccuracyorcompletenessofthecontentsofthisdocumentandreservestherightto
makechangestospecificationsandproductdescriptionsatanytimewithoutnotice.SonicWallInc.and/oritsaffiliatesdonotmakeany
commitmenttoupdatetheinformationcontainedinthisdocument.
Formoreinformation,visithttps://www.sonicwall.com/legal.
End
UserProductAgreement
ToviewtheSonicWallEndUserProductAgreement,goto:https://www.sonicwall.com/en‐us/legal/license‐agreements.Selectthelanguage
basedonyourgeographiclocationtoseetheEUPAthatappliestoyourregion.
OpenSourceCode
SonicWallisabletoprovideamachine‐readablecopyofopensourcecodewithrestrictive
licensessuchasGPL,LGPL,AGPLwhenapplicable
perlicenserequirements.Toobtainacompletemachine‐readablecopy,sendyourwrittenrequests,alongwithcertifiedcheckormoney
orderintheamountofUSD25.00payableto“SonicWallInc.”,to:
GeneralPublicLicenseSourceCodeRequest
SonicWallInc.Attn:JenniferAnderson
1033
McCarthyBlvd
Milpitas,CA95035
Legend
WARNING:AWARNINGiconindicatesapotentialforpropertydamage,personalinjury,ordeath.
CAUTION:ACAUTIONiconindicatespotentialdamagetohardwareorlossofdataifinstructionsarenotfollowed.
IMPORTANT,NOTE,TIP,MOBILE,orVIDEO:Aninformationiconindicatessupportinginformation.
